Navigating the Top Cybersecurity Risks in 2024
The threat of cybersecurity attacks is constantly evolving and accelerating. All organizations should be aware of risks specific to their company, size, and industry in order to take proactive steps to protect sensitive data. A risk register is a great way to make sure that the top risks are identified and addressed.
What is a Risk Register?
A risk register is a document or log that tracks potential risks. It typically includes information such as the nature of the risk, its likelihood, potential impact, and proposed mitigation strategies.
A robust and comprehensive risk register allows companies to identify, assess, and manage potential risks.
Four Steps to Create a Risk Register
Identify risks
Be sure to include team members from across your organization to brainstorm potential risks.
Estimate risk impact
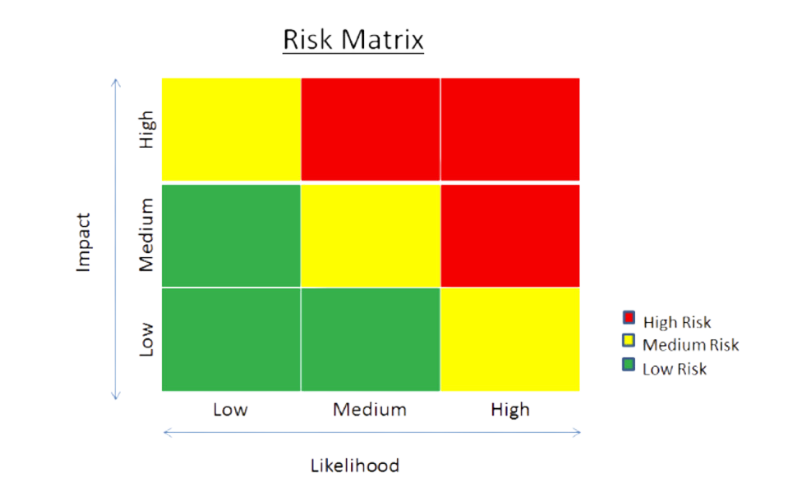
Assess the likelihood, impact, potential mitigation strategies for each risk. *See Risk Matrix example below*
Respond to each risk
Decide whether you will accept, reject, transfer, or mitigate the risk.
Define risk owners
Assign an owner to each risk.
See the end of the article for additional resources on developing a risk register.
Top Cybersecurity Risks to Consider in 2024
According to Forbes, as well as our own experiences, these are the top cyber threats that companies should be prepared for in 2024. As you develop or update your risk register, these are a great starting point.
Phishing Attacks
Phishing attacks continue to be a pervasive threat, exploiting human vulnerabilities. Companies must prioritize employee education to recognize and thwart phishing attempts, bolstered by robust email filtering systems .
Ransomware
The rise of ransomware has transformed data breaches into financial nightmares. Regular data backups, strong endpoint protection, and a well-defined incident response plan are crucial elements in mitigating the impact of ransomware attacks.
Outdated Software
Unpatched systems are low-hanging fruit for cybercriminals. Regular software updates and patch management are vital to close vulnerabilities and maintain a robust cybersecurity posture.
Insider Threats
Whether intentional or unintentional, insider threats pose a significant risk. Implementing strict access controls, monitoring employee activities, and fostering a culture of cybersecurity awareness are key measures to mitigate insider threats.
Cloud Security
As businesses embrace cloud services, securing data in shared environments becomes critical. Implementing encryption, multi-factor authentication, and thorough due diligence when selecting cloud service providers are essential components of cloud security.
Third-Party Risks
Collaborations with external vendors introduce additional risks. A thorough assessment of third-party security practices and contractual obligations can help manage and minimize associated risks.
Mobile Device Security
The increasing reliance on mobile devices demands a heightened focus on mobile security. Companies should enforce strong mobile device management policies, including device encryption, remote wipe capabilities, and secure app usage.
IoT Vulnerabilities
The proliferation of Internet of Things (IoT) devices expands the attack surface. Rigorous security protocols for IoT devices, regular updates, and network segmentation can help mitigate risks associated with connected technologies.
Social Engineering
Social engineering tactics prey on human psychology. Ongoing employee training, simulated phishing exercises, and the promotion of a skeptical mindset can fortify defenses against social engineering attacks.
Weak Passwords
Passwords remain a common point of vulnerability. Encourage strong, unique passwords, implement multi-factor authentication, and regularly audit user access to fortify the first line of defense.
The Bottom Line
A proactive cybersecurity approach is essential for businesses to protect against potential threats. By acknowledging and addressing these top cybersecurity risks in their risk register, companies can strengthen their defenses, safeguard sensitive information, and mitigate impact.

