Cyber Intelligence Weekly (March 3, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight our vCISO led Security Team as a Service (StaaS)!
🌍 Introducing #STaaS by Echelon Risk + Cyber! 🛡️
🔐 Elevate your #cybersecurity with our complete team of pros, led by a seasoned #vCISO. #STaaS is your strategic shield, offering 24/7 protection and navigating compliance complexities with ease.
Echelon's #STaaS isn't just a service; it's your digital fortress in a world where #CyberSecurity is paramount. From complex compliance landscapes to defending against sophisticated threats, our team is your frontline defense.
🚫 Don't leave your cybersecurity to chance. Dive into how we can transform your cyber strategy and safeguard your future by reading our Cybersecurity Dive Press Release here: https://lnkd.in/eRc93wi2

Before we get started on this week’s CIW, I’d also like to highlight a solution from one of our strategic technology partners. This week, we highlight…

KnowBe4 Security Awareness Platform
Echelon Risk + Cyber proudly cultivates a diverse network of strategic relationships with leading vendors in the cybersecurity industry. These collaborations empower Echelon to deliver premium services to our clients through cutting-edge technology and valuable insights. In our ongoing effort to bring top-shelf knowledge, each week we want to spotlight a distinguished partner solution offered at Echelon. This week’s focus is on KnowBe4’s Security Awareness Training Platform.
KnowBe4 stands out as a premier security awareness training platform, dedicated to empowering organizations in proactively educating their employees about the ever-evolving landscape of phishing techniques. Recognizing that human error remains a constant vulnerability, KnowBe4 addresses the persistent threat of social engineering attacks, wherein employees can inadvertently become the weakest link with a simple click or file download. This is where KnowBe4's expertise proves invaluable.
One of the standout features of KnowBe4 is its ability to conduct interactive and automated training campaigns. These campaigns are tailored to specific roles and responsibilities within an organization, or they can be rolled out on a broader scale across the entire workforce. This personalized approach ensures that employees receive relevant and targeted training to enhance their awareness and resilience against cyber threats.
KnowBe4's platform also distinguishes itself by offering a plethora of simulated social engineering attacks through various channels, including email, phone, and text. This multifaceted approach enables organizations to assess and fortify their defenses against a diverse range of cyber threats. By exposing employees to realistic simulations, KnowBe4 helps them recognize and respond to potential threats effectively, thereby reducing the risk of falling victim to actual social engineering attacks.
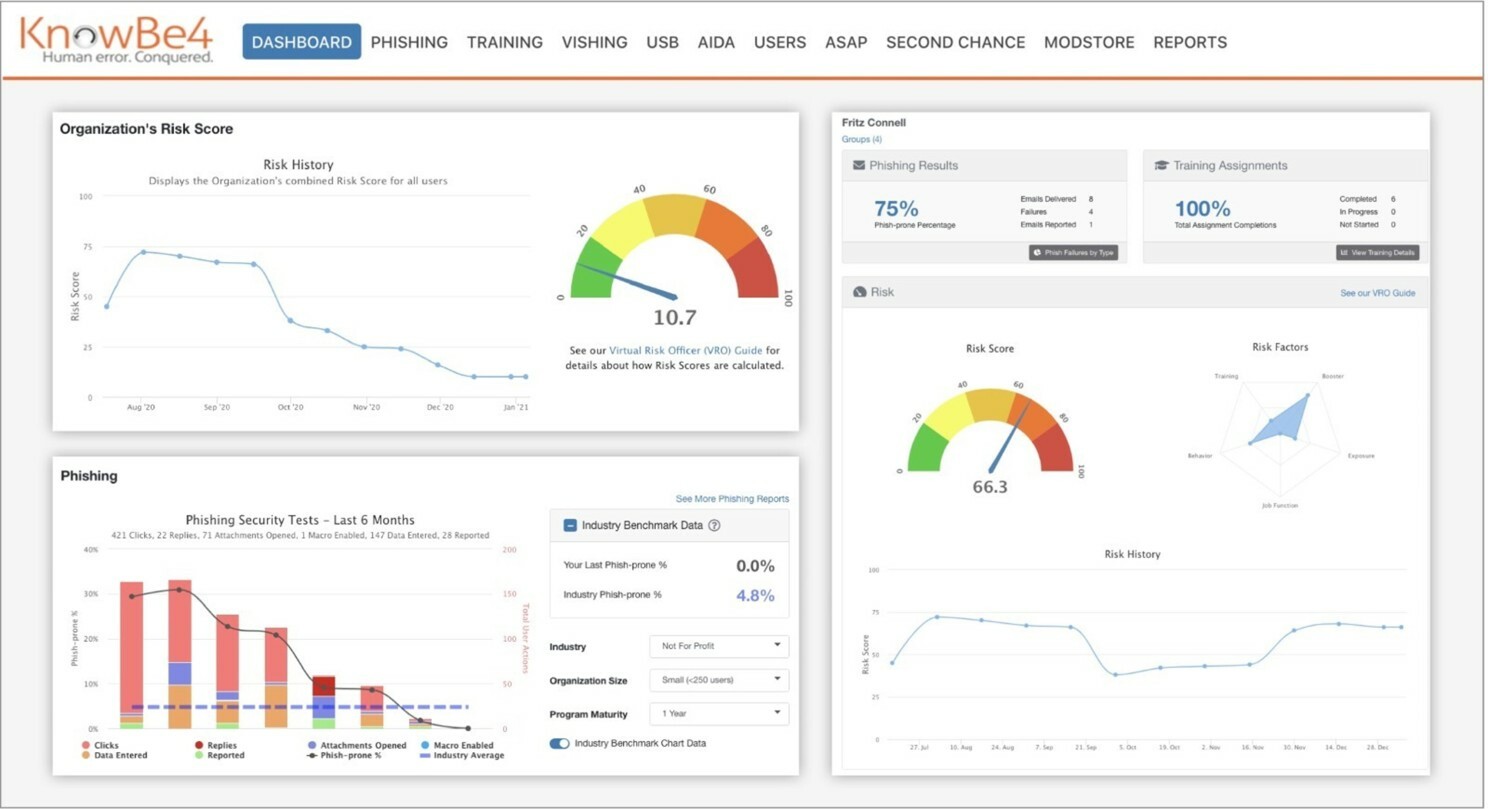
KnowBe4's commitment to holistic cybersecurity extends to an interactive and highly valuable dashboard. This dashboard serves as a nerve center, providing real-time reporting on the organization's risk score. Beyond just numbers, it offers a granular view of training assignments, showcasing the individuals who have successfully completed them and those who may require additional attention. This level of visibility empowers organizations to manage risk proactively, allowing for strategic interventions and targeted support where needed.
With the conclusion of the insight into KnowBe4’s Platform, we look ahead with anticipation. Echelon Risk + Cyber remains dedicated to pushing the boundaries of cybersecurity innovation, forging partnerships that empower us to stay at the forefront of industry trends. If your organization is grappling with specific security challenges, allow Echelon to help alleviate the burden. Reach out to discuss how we might help your organization and stay tuned for more solution highlights in the weeks to come!
Away we go!
1. NIST Unveils CSF 2.0: A New Chapter in Cybersecurity Framework Evolution
The National Institute of Standards and Technology (NIST) has introduced Version 2.0 of its Cybersecurity Framework (CSF), marking the framework's first significant update since its inception in 2014. This latest version broadens its applicability beyond the original focus on critical infrastructure to include organizations of all sizes and sectors. The revamped CSF now offers a comprehensive approach to managing and mitigating cybersecurity risks, emphasizing governance and supply chain security. The expansion and modification of the CSF reflect feedback from a wide range of stakeholders and aim to provide organizations with a more versatile set of tools to address the evolving landscape of cybersecurity threats.
NIST's CSF 2.0 includes enhancements to the core guidance and introduces a variety of resources designed to help organizations tailor their cybersecurity strategies to their specific needs. Among these new tools are quick-start guides, success stories demonstrating practical applications of the framework, and a searchable catalog of informative references that link the CSF's guidance to over 50 other cybersecurity documents. The addition of the "Govern" function to the framework's core underscores the importance of integrating cybersecurity considerations into the broader context of enterprise risk management, highlighting the role of senior leadership in cybersecurity decision-making.
The CSF 2.0 also simplifies the implementation process, offering a new reference tool that facilitates the exploration, search, and exportation of data from the framework in both human-consumable and machine-readable formats. This update is part of NIST's ongoing effort to make the CSF an invaluable resource for a wider audience, both in the United States and internationally. By encouraging feedback and sharing of best practices within the user community, NIST aims to continuously refine the framework, helping organizations, sectors, and nations enhance their cybersecurity resilience.
2. Urgent Warning: Cyber Threats Targeting Ivanti Gateways Exposed
Cybersecurity agencies, including CISA and international partners, have issued a joint advisory warning that cyber threat actors are exploiting known vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure gateways. These vulnerabilities, identified as CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893, affect all supported versions of the software and allow attackers to bypass authentication, craft malicious requests, and execute commands with elevated privileges. Despite efforts to detect compromises using Ivanti’s Integrity Checker Tool (ICT), it has been found that the tool fails to recognize when systems have been compromised, allowing threat actors to maintain root-level persistence even after factory resets.
The advisory strongly urges network defenders to assume that credentials within the affected Ivanti VPN appliances are likely compromised and to actively search for signs of malicious activity on their networks. Organizations are advised to use the latest version of Ivanti's external ICT, apply patches as they become available, and follow incident response recommendations provided in the advisory. Given the sophistication of the threat actors involved and their ability to remain undetected for extended periods, the safest course of action may involve assuming that compromised devices could harbor rootkits that remain active even after resets.
This situation underscores the significant risks posed by these vulnerabilities and the sophisticated nature of the cyber threat actors exploiting them. Organizations using Ivanti Connect Secure and Ivanti Policy Secure gateways are encouraged to take immediate steps to mitigate these risks, including considering the removal of affected devices from their networks if persistent threats cannot be confidently eradicated. The advisory is part of a broader effort to address cybersecurity vulnerabilities and protect critical infrastructure from sophisticated cyberattacks.
CISA advises the follow if a potential compromise is detected:
1) Quarantine or take offline potentially affected hosts.
2) Reimage compromised hosts.
3) Reset all credentials that may have been exposed during the compromise, including user and service accounts.
4) Identify Ivanti hosts with Active Directory (AD) access, threat actors can trivially export active domain administrator credentials during initial compromise. Until there is evidence to the contrary, it is assumed that AD access on compromised systems is connected to external authentication systems such as Lightweight Directory Access Protocol (LDAP) and AD.
5) Collect and review artifacts such as running processes/services, unusual authentications, and recent network connections. Note: Removing malicious administrator accounts may not fully mitigate risk considering threat actors may have established additional persistence mechanisms.
6) Report the compromise to FBI Internet Crime Complaint Center (IC3) at IC3.gov, local FBI field Office, or CISA via the agency’s Incident Reporting System or its 24/7 Operations Center ([email protected] or 888-282-0870). State, local, tribal, or territorial government entities can also report to MS-ISAC ([email protected] or 866-787-4722). Organizations outside of the United States should contact their national cyber center. (See the Reporting section.)
3. Millions of Malicious Forks, GitHub's Battle Against Hidden Malware
GitHub, the popular code hosting platform, is currently facing a significant cybersecurity challenge as it deals with an onslaught of malicious repositories. These repositories, numbering in the millions, are cleverly disguised as legitimate forks of genuine code bases but are actually laced with malware designed to steal passwords and cryptocurrency from unsuspecting developers. This sophisticated attack involves the automated process of forking real repositories and embedding a malicious payload beneath layers of obfuscation. Despite GitHub's efforts to remove these repositories, the scale of the attack means that thousands remain active, posing a risk to users who might inadvertently fork these tainted versions, further propagating the malware.
The attack exploits human error and social engineering rather than software vulnerabilities, making it particularly insidious. Developers might choose a malicious repository over the genuine one due to its identical name or through being misled by promotions on various web forums and social platforms. Once a developer interacts with one of these repositories, the malware executes, harvesting sensitive information and sending it back to the attackers. The security community, including researchers from Apiiro and others, have traced the campaign's evolution over several months, noting its increasing sophistication and the challenges in combating such a widespread and automated threat.
GitHub's struggle against this wave of malware highlights the ongoing battle between cybersecurity measures and the evolving tactics of cybercriminals. The attack, dubbed "repo confusion," takes advantage of the trust placed in the platform's repository system, demonstrating the need for heightened vigilance among developers and the importance of verifying the authenticity of code sources. As GitHub and its community work to identify and remove these malicious repositories, the incident serves as a reminder of the constant vigilance required to protect against cyber threats in today's interconnected digital landscape.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
