Cyber Intelligence Weekly (August 28, 2022): Our Take on Three Things You Need to Know
Before we get started on this week’s CIW, I’d like to highlight this article from my colleague Tom Garrubba where he so cleverly uses this well-known thrill ride safety mechanism as an analogy to vendor management and sharing your most precious data with third parties. Well timed with the wind down of summer.

Away we go!
1. Popular Password Manager LastPass Suffers Security Incident
One of the most popular password manager solutions on the market confirmed via a blog post that they experienced a cybersecurity incident last week. A password manager is a software application that allows users to store, generate, and manage their passwords for websites, local applications and more. Password managers can assist users with generating and retrieving complex passwords, storing passwords securely in an encrypted database, or even helping users create passwords on demand.
Password managers are popular security mechanisms because they help fight common user behavior. They can help users create strong and effective passwords with adequate complexity, but even more importantly, long length. In most cases, with a password manager the user doesn’t have to remember their passwords because the password manager automatically fills them in the browser, according to settings. In addition, password managers like LastPass can help combat password reuse, effectively ensuring the same password is not used in several places.
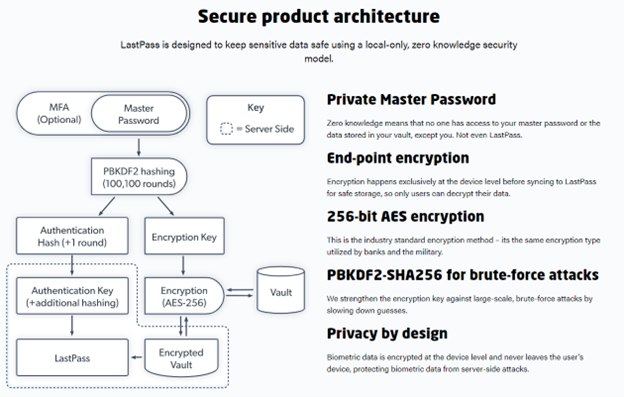
Source: LastPass.co
The details of the computer security incident noted on the blog post state that the threat actor gained unauthorized access to portions of the LastPass developer environment through compromise of a single developer account. LastPass notes that the threat actor took portions of source code and other proprietary technical information but that was the extent of the incident. They came out and said that user vault data nor user master key data was affected as part of this incident. The LastPass security measures are architected in such a way that the user’s master password is the key that hashes/encrypts the user data vault with AES 256 encryption. All of that happens locally on the end user device as well. Basically, even LastPass can’t access your secret data if they wanted to.
While all signs point to zero user impact from this LastPass incident, it surely has raised a ton of concern in the community. Hopefully this is indeed a near miss from a user impact perspective and the story ends here. This highlights the wide scale reliance on these types of systems and how their compromise could be catastrophic in terms of sheer size and scale.
2. Mudge has some Serious Twitter Beef
A recent story from the Washington Post drops a whistleblower report that lays out a series of potential major security and privacy issues at Twitter that have reportedly been covered up or downplayed by senior management over time.
Peiter “Mudge” Zatko was hired by Jack Dorsey in 2020 to help clean up after the massive July 15th incident where teenage hackers took over the Twitter accounts of politicians, celebrities, and entrepreneurs, including Barack Obama, Kim Kardashian West, Jeff Bezos, and Elon Musk. Mudge worked at Twitter up until January 19, 2022 when he was fired.

The Washington Post published Mudge’s whistleblower complaint to the SEC. The complaint outlines a long list of issues, here are some of the highlights:
- The complaint alleges that Twitter intentionally reports bots as part of their monetizable daily active users. Mudge even states that the Twitter CEO Parag Agrawal lied on Twitter, when he stated Twitter executives are incentivized to detect or report spam bots on the platform. This could be music to Elon Musk’s ears as he is trying to squash the Twitter takeover deal he has brewing due to the fact that he believes there are more bots on the site than Twitter is letting on.
- Cybersecurity and privacy risk issues that Mudge had identified during his time at Twitter were either held back from being reported to the board or they were sanitized to downplay the true issues at hand. Mudge asserts that the current CEO of Twitter instructed him to provide the board with misleading materials.
- The report also claims that Twitter was pressured into hiring two Indian agents and giving them access to sensitive Twitter data and systems.
- Mudge also claims that administrative access to Twitter’s most critical systems is wide open and can be accessed broadly, by nearly half of the employees at Twitter.
- Twitter was never in compliance with the 2011 FTC consent order.
- Over 50% of Twitter’s 500,000 data center servers had non-compliant kernels or out of date operating systems
This one will be interesting to watch unfold. Mudge will be testifying before congress sometime next month, so stay tuned.
3. Roasting 0ktapus: The Phishing Campaign Going after Okta Identity Credentials
Apparently the Twilio and Signal issue that we wrote about goes much farther than those two organizations. After seeing the reports on Signal, Group-IB Threat Intelligence decided to publicly release a report last week based on the research that they have been performing.
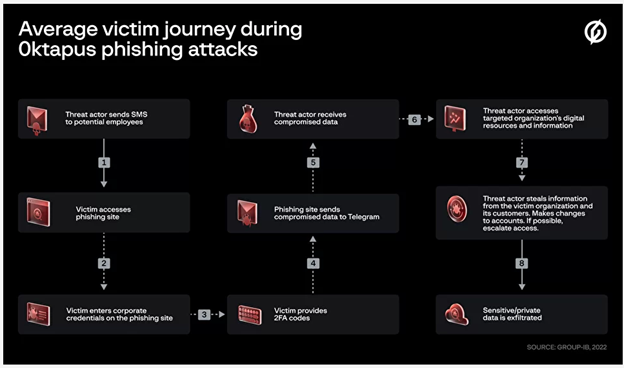
Source: Groub-IB
Group-IB has been targeting employees of companies that use Okta, a popular IAM tool. Essentially the attacks they launched in all these instances were fairly low-tech but effective nonetheless. They sent SMS phishes, tricking users into accessing a look-a-like site where they would enter their corporate credentials, capture their MFA prompt and then the threat actor is in.
Per the Group-ID report the majority of the 130 companies targeted were SaaS and software companies in the US. Victims in the attackers campaign include Doordash, as well as email marketing firms Klaviyo and Mailchimp. In each of these cases, the crooks made off with names, addresses, emails, and phone numbers of their customers. This situation shows the wide scale trouble that social engineering can cause. It is important that users always carefully check any URLs before they click on them, especially if it is a user with a privileged account. In addition, having a strong second factor of multi-factor authentication, such as a FIDO-2 compliant security key is highly advisable to thwart these types of attacks. Push based forms of MFA are prone to theft, as highlighted by these attackers.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about

