Cyber Intelligence Weekly (August 20, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight this article written by Dahvid Schloss where you can learn the real differences between red teaming and penetration testing. You'll discover how these terms are often misused and the consequences this confusion has on security:
- Penetration Testing vs. Red Teaming: Demystified
- Red Team Assessments: Unveiling the True Goals
- The Danger of Mixing Up Terms: A Wake-Up Call
- Navigating Security Terminology: Expert Insights
Don't let vague definitions compromise your organization's safety. Arm yourself with knowledge and empower your cyber strategy!

Away we go!
1. Brunswick in Rough Waters: Unraveling the $85 Million Cyberattack Impact
Brunswick Corporation, a leading marine industry firm with operations in 24 countries, is facing financial repercussions of up to $85 million following a cybersecurity breach. The billion-dollar boating manufacturing company, which reported nearly $6 billion in revenue in 2021, revealed the cyberattack on June 13. While Brunswick officials did not specify the type of the attack, operations at several locations were halted as cybersecurity experts and law enforcement stepped in, many clear indicators of a possible ransomware attack.
The cyber incident significantly disrupted the company's second quarter financial performance. CEO Dave Foulkes informed investors and board members that the Q2 financial results came in below initial projections. Foulkes highlighted the severe disruption, especially in the Propulsion and Engine Parts & Accessories segments, stating the incident's timing, close to the quarter's end, left minimal chances for recovery within that timeframe.
On June 13, we announced that we’ve been impacted by an IT Security Incident, which ultimately resulted in second quarter financial results that were lower than initial expectations. The disruption associated with the IT security incident was the most significant in our Propulsion and Engine Parts & Accessories segments. And because of the proximity to the end of the quarter, there was limited opportunity to recover fully within the same period. Within nine days, the company announced that all primary global manufacturing and distribution facilities were fully operational with no significant residual impacts. We have the opportunity to recover some lost production and distribution across our businesses, which will partially offset lost days in the second quarter.
However, lost production days on high horsepower outboard engines will be challenging to recover because the production schedule was already full for the balance of the year. We estimate the financial impact to be approximately $80 million to $85 million of revenue in the quarter and $60 million to $70 million for the full year. I’ll turn now to some of the segment highlights that facilitated a solid second quarter. Prior to the disruption from the IT Security Incident, our high horsepower outboard engine production ramp-up was progressing and has since resumed, allowing us to increase shipments to repower customers and OEM partners. Mercury Marine continues to expand outboard Propulsion and retail market share around the globe. Demonstrating the strength of our comprehensive Propulsion product portfolio.
Notably, the company took nine days to fully resume operations. While some lost production and distribution can be recuperated, Foulkes mentioned the production schedule for high horsepower outboard engines, already packed for the year, might be challenging to restore.
Further financial strains were felt at Navico, a marine electronics firm acquired by Brunswick in 2021. According to Chief Financial Officer Ryan Gwillim, the downtime at Navico was responsible for financial losses of about $13 million. Interestingly, no hacker or ransomware group has yet claimed responsibility for this breach. This incident aligns with a growing trend of cyberattacks targeting manufacturing enterprises.
Brunswick initially reported the breach through the above linked Press Release as well as to the SEC and investors through Form 8-K on June 14, 2023.
2. Chinese Hackers Compromise State Department & GOP Congressman Emails
Recent investigations have unveiled that suspected Chinese hackers were behind a significant email breach that targeted the State Department and GOP Congressman Don Bacon. The hackers exploited a vulnerability in Microsoft's system, masquerading as verified customers to access protected information between mid-May and mid-June. Rep. Bacon, a strong advocate for Taiwan and a member of the House Armed Services Committee, stated that he believed the intention behind the hack was to politically undermine or embarrass him. Despite the hacking attempt, Bacon has reaffirmed his commitment to supporting an aid package for Taiwan.
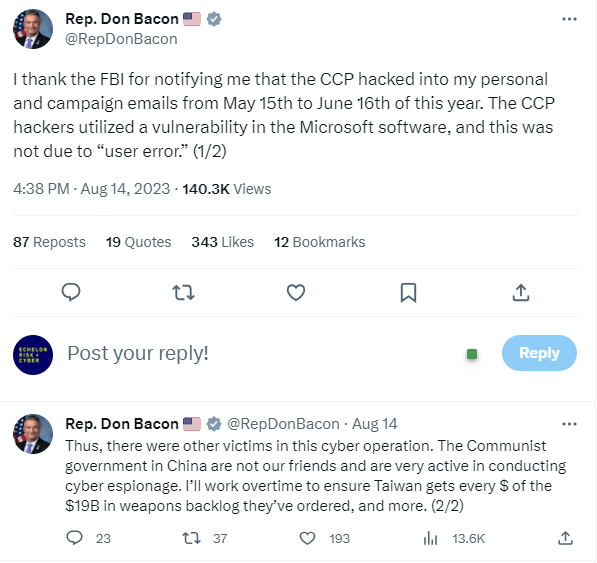
The Microsoft vulnerability has raised concerns among cybersecurity experts. The ability of hackers to bypass multifactor authentication, potentially exposing millions to threats, has highlighted the government's heavy reliance on Microsoft for essential cloud and email services. Though Microsoft identified and blocked the hackers' master key after the State Department detected suspicious activity, lawmakers are demanding answers. Several members of Congress are urging for strategies to thwart similar future attacks, and for Microsoft to enhance transparency around its activity logs.
Adding to the gravity of the situation, Sen. Ron Wyden has requested the Justice Department and the Federal Trade Commission to investigate Microsoft's security measures. He questions whether Microsoft may have violated laws or older agreements that mandated enhanced security. Amid these concerns, the Department of Homeland Security's Cyber Safety Review Board has announced it will examine the breach further. This one will definitely be interesting to follow.
3. Urgent Warning Issued Over Citrix ShareFile Vulnerability
Recent activities highlight a surge in the exploitation of a vulnerability in Citrix ShareFile, leading the US Cybersecurity and Infrastructure Security Agency (CISA) to issue an urgent warning. The vulnerability, designated as CVE-2023-24489, has been labeled 'critical' and can permit an unauthenticated user to upload arbitrary files, potentially gaining remote code execution. The flaw in the ShareFile file sharing system was first unveiled by Assetnote researchers in early July, revealing that up to 6,000 ShareFile instances might be exposed on the internet. This vulnerability affects all currently supported versions of customer-managed ShareFile storage zones controller before version 5.11.24. This only applies to independently managed ShareFile storage zones controllers. Citrix customers using ShareFile-managed storage zones in the cloud do not need to take any action.
Citrix promptly responded with patches for CVE-2023-24489 on June 13. However, exploitation activities began to emerge by late July. Notably, threat intelligence agency GreyNoise identified attack attempts originating from a select group of IP addresses. The situation escalated rapidly as CISA integrated CVE-2023-24489 into its Known Exploited Vulnerabilities Catalog on a recent Wednesday, setting a deadline for government entities to rectify the issue by September 6. Concurrently, GreyNoise reported a significant rise in exploitation attempts involving 72 unique IP addresses.
The motivations behind these attacks remain unclear. Still, it's crucial to understand that Citrix vulnerabilities have previously been a target for both financial cybercriminals and state-sponsored entities. This escalation follows closely on the heels of another alarming report by NCC Group, which identified 2,000 backdoored Citrix NetScaler instances due to another recent vulnerability, CVE-2023-3519. For remediation actions and suggestions, please refer to the Citrix blog.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
