Cyber Intelligence Weekly (February 25, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight our vCISO led Security Team as a Service (StaaS)!
🌍 Introducing #STaaS by Echelon Risk + Cyber! 🛡️ 🔐 Elevate your #cybersecurity with our complete team of pros, led by a seasoned #vCISO. #STaaS is your strategic shield, offering 24/7 protection and navigating compliance complexities with ease. Echelon's #STaaS isn't just a service; it's your digital fortress in a world where #CyberSecurity is paramount. From complex compliance landscapes to defending against sophisticated threats, our team is your frontline defense. 🚫 Don't leave your cybersecurity to chance. Dive into how we can transform your cyber strategy and safeguard your future by reading our Cybersecurity Dive Press Release here: https://lnkd.in/eRc93wi2

Before we get started on this week’s CIW, I’d also like to highlight a solution from one of our strategic technology partners. This week, we highlight…
Expel MDR Platform

Echelon Risk + Cyber proudly cultivates a diverse network of strategic relationships with leading vendors in the Cybersecurity Industry. These collaborations empower Echelon to deliver premium services to our clients through cutting-edge technology and valuable insights. In our ongoing effort to bring top-shelf knowledge, each week, we want to spotlight a distinguished partner solution offered at Echelon. This week’s focus is on Expel’s Managed Detection and Response (MDR) Platform.
The Expel Platform provides an efficient solution for incident resolution through its Managed Detection and Response (MDR) service, centered around the Expel Workbench Security Operations platform. With an automated approach, alerts are swiftly analyzed in under 1 minute, offering context and enriching the interface with intelligence to assess risks. Expel follows a Bring Your Own Tech (BYO-tech) MDR approach, enabling seamless integration with a broad array of security technologies.
The platform effortlessly integrates with existing technologies, including Tenable, Rapid7 Scanner, Azure, and more, without the need for additional hardware or a Security Information and Event Management (SIEM) system. Expel extends its detection and response capabilities across Cloud platforms, Kubernetes, SaaS Applications, and On-Premise environments.
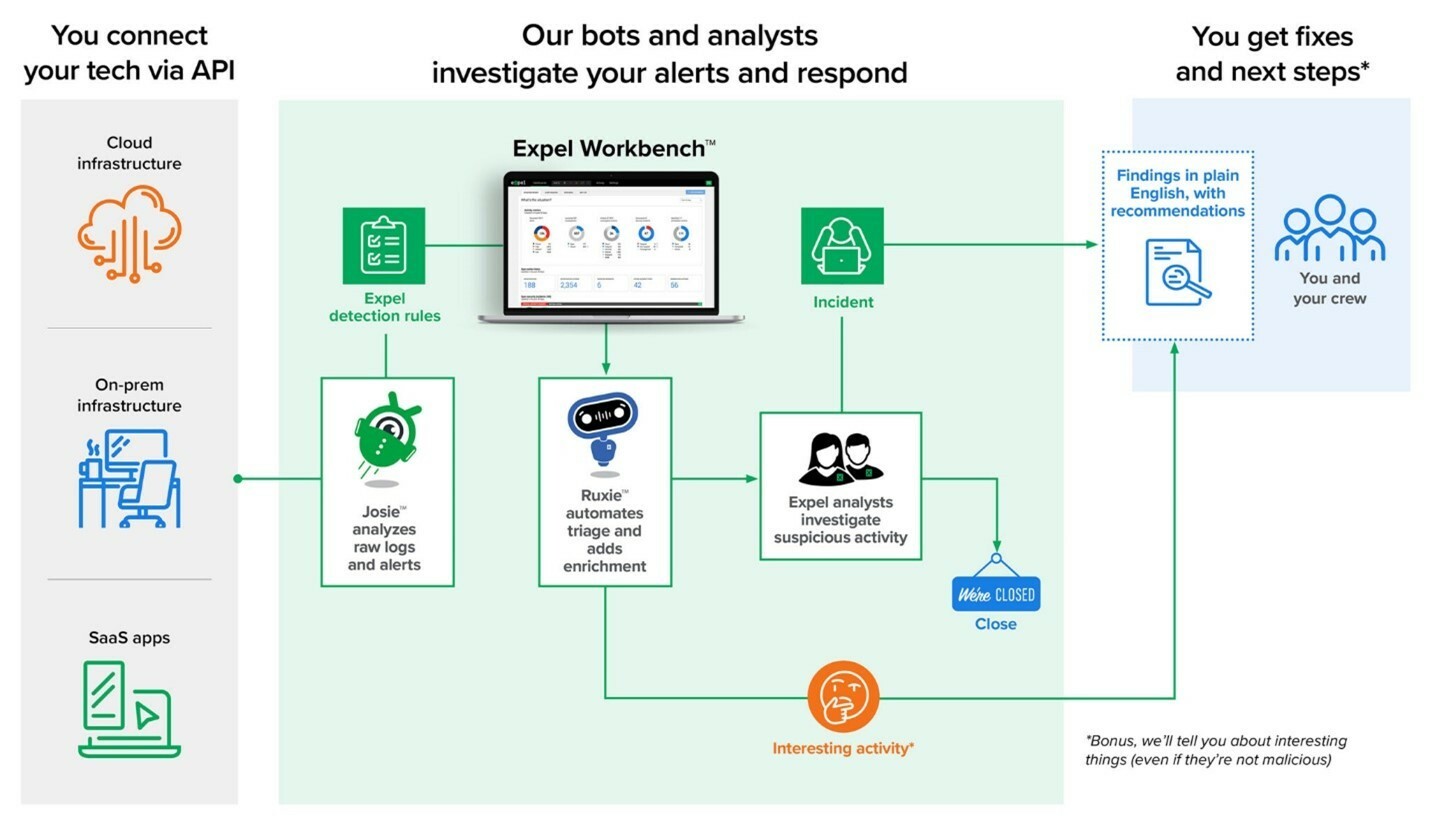
Expel not only applies custom detections but also leverages insights gained from data to enhance the overall detection and response capabilities, resulting in a positive Return on Investment (ROI). Automation is judiciously deployed, automating logs and alerts for swift resolution, or providing resilience recommendations. Expel’s Security Operations Center strategically focuses on investigating only pertinent events, eliminating noise, and ensuring immediate attention to critical alerts. Furthermore, Expel enhances its detection and response capabilities with Vulnerability Prioritization, offering transparency through real-time alerts and intuitive reporting for ongoing risk prevention. To top it all off, Echelon offers a Tier 3 support model through Echelon’s SOC + service, contact us to learn more!
With the conclusion of the insight into Expel’s MDR Platform, we look ahead with anticipation. Echelon Risk + Cyber remains dedicated to pushing the boundaries of cybersecurity innovation, forging partnerships that empower us to stay at the forefront of industry trends. If your organization is grappling with specific security challenges, allow Echelon to help alleviate the burden. Reach out to discuss how we might help your organization and stay tuned for more solution highlights in the weeks to come!
Away we go!
1. U.S. and U.K. Join Forces to Neutralize LockBit Ransomware Operations
In a landmark collaborative effort, the Department of Justice, alongside the United Kingdom and other international law enforcement agencies, has significantly disrupted the operations of the LockBit ransomware group, a notoriously active cybercriminal gang. This group, responsible for targeting over 2,000 victims worldwide and extracting more than $120 million in ransom payments, was dealt a severe blow through the seizure of its public-facing websites and server infrastructure. These actions have hindered LockBit's ability to launch new attacks and extort their victims, marking a critical step in combatting global cybercrime.
The operation not only dismantled LockBit's capacity for further harm (for now) but also led to the indictment of two Russian nationals, Artur Sungatov and Ivan Kondratyev, for their involvement in deploying the LockBit ransomware across various industries in the United States and internationally. This indictment underscores the global nature of cyber threats and the necessity for international cooperation in addressing these challenges. Additionally, the operation has enabled the recovery of decryption keys, offering a lifeline to hundreds of victims worldwide by potentially restoring access to their encrypted systems.
This strategic takedown exemplifies the determination and collaborative spirit of law enforcement agencies across the globe to disrupt cybercriminal activities and protect citizens and businesses from the devastating impacts of ransomware attacks. The initiative not only showcases the technical prowess and investigative capabilities of these agencies but also serves as a warning to cybercriminals everywhere that their actions will not go unpunished. As the fight against cybercrime continues, this operation stands as a testament to what can be achieved when nations unite against a common adversary. It will be interesting to see if there are lasting effects from this law enforcement win or if the group will come back even stronger than before.
2. The I-Soon Leak and the Glimpse into China's Surveillance State
There is certainly no shortage of blockbuster stories this week! In our next summary, I highlight a significant leak involving a private security contractor linked to China's Ministry of Public Security that has accidentally unveiled a plethora of documents detailing the state's surveillance activities, both domestically and internationally. This unauthorized release, which includes hacking tools and espionage tactics, highlights the pervasive nature of China's surveillance operations targeting dissidents, ethnic minorities, and foreign entities. The contractor, known as I-Soon (Anxun in Mandarin), has been implicated in spying activities across regions known for anti-government protests, such as Hong Kong and Xinjiang, as well as hacking efforts in Central and Southeast Asia, and even the self-ruled island of Taiwan. The documents expose how I-Soon's technology has been utilized by Chinese state agents to infiltrate social media platforms, breach email accounts, and mask the online presence of overseas operatives, raising significant concerns about privacy and security on a global scale.
The revelation of these documents has prompted an investigation by Chinese authorities and I-Soon, amid fears of the potential impact on their operations. The leak, described by cybersecurity experts as one of the most significant of its kind, underscores the extensive reach of China's surveillance and its efforts to control dissent beyond its borders. The materials provide detailed insights into the methods employed by the Chinese government to monitor critical voices on international social media platforms, where Chinese users often seek refuge from state censorship. The implications of such widespread surveillance are profound, affecting not just the targeted individuals and organizations but also the broader international community's perception of privacy and security in the digital age.
This incident has sparked debate over the source of the leak, with speculation ranging from internal dissension within I-Soon to strategic leaks by foreign intelligence services. The exposure of these activities poses a challenge to China's international relations, particularly as it pertains to cybersecurity and espionage. It also highlights the ongoing tensions between China and the West over cyber operations, with both sides accusing each other of malicious activities in cyberspace. It also serves as a stark reminder, and perhaps the most public inside look, at a national cyber apparatus that is viewed as a national imperative for China to dominate the cyber information wars.
3. Cybersecurity Company, Avast, Faces $16.5 Million Fine for Selling User Browsing Data
Avast, a well-known cybersecurity company, has been fined $16.5 million by the Federal Trade Commission (FTC) for its practices concerning user data privacy. Between 2014 and 2020, Avast collected extensive web browsing data from its users through its antivirus software and browser extensions, without their explicit consent. This data included sensitive information such as religious beliefs, health concerns, political affiliations, geographic locations, and financial situations. Despite Avast's claims of anonymizing this data before selling it to third parties, the FTC discovered that the data sold included unique identifiers that could easily trace back to individual users, effectively compromising their privacy.
The investigation, initially sparked by reports from Motherboard and PCMag in 2020, led to Avast shutting down Jumpshot, its data-selling subsidiary. However, the FTC's complaint highlighted that Avast not only failed to adequately protect user privacy but also misled users by claiming its software would eliminate web tracking, whereas it was actually conducting the tracking itself. As part of the settlement, Avast is now prohibited from misrepresenting the nature of their data collection and usage, and from selling or licensing browsing data for advertising purposes. Furthermore, Avast is required to delete all web browsing data previously collected by Jumpshot and to inform affected customers of the unauthorized data sales.
This case underscores a growing concern over digital privacy and the measures regulatory bodies are willing to take to protect consumers. Avast's statement expressed disagreement with the FTC's allegations but confirmed their commitment to resolving the matter and continuing their mission to protect users' digital lives. This incident is part of a broader FTC crackdown on companies that misuse personal data, signaling a tougher stance on privacy violations in the digital age.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about

