Cyber Intelligence Weekly (July 23, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to make a significant announcement!
Echelon Risk + Cyber Welcomes Chad LeMaire as Chief Security Officer
Pittsburgh, PA / 23 July 2023 – Echelon Risk + Cyber, a cybersecurity professional services firm, today announced the addition of Chad LeMaire as Chief Security Officer. Chad is a veteran who served in senior executive cybersecurity roles including the Air Force Special Operations Command, Pacific Air Forces, and U.S. Indo-Pacific Command. As CSO, Chad will offer strategic advisory to Echelon clients and lead client-facing offensive and defensive security teams.
Chad is an accomplished senior cybersecurity executive and CIO with more than 30 years of experience leading large organizations and teams, as well as directing strategic cybersecurity efforts. He has held multiple senior level cybersecurity roles for large organizations where he identified cybersecurity gaps, authored strategies, and implemented cybersecurity capabilities. He was a qualified cyber warfare officer in the U.S. Air Force, commanded the Air Force Blue Team, and led cyber incident responses and vulnerability assessments on critical networks and systems within the Department of Defense. Chad pioneered the development of cyber protection teams and the concept of the Director of Cyber Forces within the Air Force. He also built and led small teams and large organizations which conducted offensive, defensive, and cybersecurity operations.

“We are excited and humbled to add someone of Chad’s caliber to our already high-performing team,” said Dan Desko, CEO of Echelon Risk + Cyber. “His unparalleled leadership combined with deep cybersecurity expertise and exemplary service to our country make him the perfect match for Echelon and our clients as we double down on our commitment to protect the basic human right to security and privacy.”
“Echelon’s mission, vision and values are extremely aligned with my passions for helping organizations improve their cybersecurity, and for growing and mentoring people,” said LeMaire. “I’m excited about the opportunity to help Echelon expand into new industries, develop our internal teams, and help our clients operationalize cybersecurity to make it part of their culture.”
Away we go!
1. Underestimating the Threat: The True Reach of the Compromised Microsoft Key
Last week we wrote about how Microsoft and CISA disclosed a security incident that impacted customers of Exchange Online and Outlook.com. The incident, attributed to a threat actor known as Storm-0558 from China, involved the acquisition of a private encryption key (MSA key) to forge access tokens for Outlook Web Access (OWA) and Outlook.com. While Microsoft initially stated that only these two applications were affected, new research from Wiz found that the compromised MSA key could have much broader implications. This breach could have allowed the threat actor to forge access tokens for various Azure Active Directory applications, including SharePoint, Teams, OneDrive, and more.
The impact of this security incident is potentially very significant, as identity provider's signing keys are among the most powerful secrets in the modern world, granting immediate access to sensitive accounts and data. While Microsoft mitigated the risk by revoking the compromised encryption key, customers might struggle to detect forged tokens against their applications due to a lack of logs on crucial fields related to token verification.
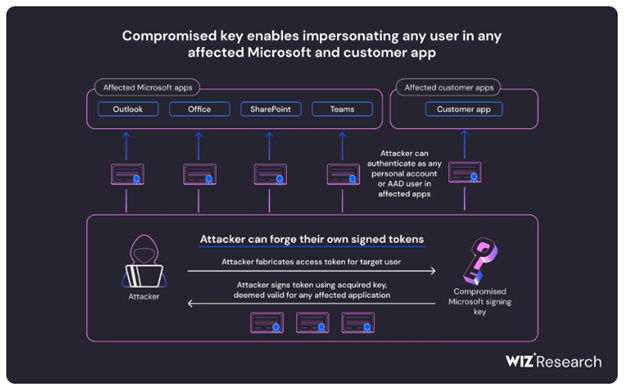
The compromised MSA key posed risks to different types of users, depending on the application they were using and whether proper token validation was in place. Users of Microsoft applications like Outlook, SharePoint, and Teams, as well as those who accessed customer applications with "Login with Microsoft" functionality, are potentially at risk. Azure Active Directory accounts in multi-tenant applications are also potentially vulnerable to impersonation based on the Wiz research.
Key forging techniques used by the threat actor may have involved crafting forged access tokens using the compromised key to impersonate users. While customers are no longer at risk from the compromised key due to Microsoft's actions, applications that retain cached or local copies of the Azure Active Directory public keys could remain susceptible.
To protect against potential threats, Microsoft advised updating the Azure SDK to the latest version, refreshing the cache of trusted certificates, and monitoring application-specific logs for signs of token forgery. Cooperation between cloud service providers and security researchers is crucial to addressing such incidents and improving cloud security.
2. North Korea-Backed Hackers Breach JumpCloud to Target Cryptocurrency Clients
Reports have surfaced in a concerning development for U.S. enterprise software company JumpCloud, who recently revealed that its systems were breached in June by a nation-state actor. Security researchers, including cybersecurity firm CrowdStrike, have now attributed the hack to Lazarus, a North Korea-backed hacking group notorious for targeting cryptocurrency entities. JumpCloud, known for its directory platform that manages user authentication and device authorization, confirmed the breach and reset customers' API keys to contain the attack.
CrowdStrike has linked the attack to "Labyrinth Chollima," a sub-group of Lazarus, known for recent supply-chain attacks on enterprise phone maker 3CX. Lazarus has a history of targeting individuals in the cryptocurrency sector, using crypto-stealing operations to fund North Korea's nuclear weapons program, which has been sanctioned by the international community.
Other security researchers have corroborated the findings, stating that the indicators of compromise (IOCs) shared by JumpCloud were connected to a range of activities attributed to North Korea. The hackers may also be linked to a recent social engineering campaign targeting GitHub customers. The GitHub alert indicated that the targeted personal accounts belonged to technology firm employees in the cryptocurrency, blockchain, and online gambling sectors, associated with a group known as TraderTraitor, supporting North Korean objectives.
JumpCloud confirmed the findings of their incident response partner, CrowdStrike, and also revealed that only a small number of customers and devices were compromised. As a widely-used software platform, JumpCloud serves over 180,000 organizations and has over 5,000 paying customers.
The incident raises concerns over the threat posed by North Korean hackers and their focus on cryptocurrency targets. In response, the U.S. government has imposed sanctions against North Korea's illicit IT workers and is offering substantial rewards for information that can help disrupt their activities. The breach highlights the importance of robust cybersecurity measures for organizations, especially those operating in the cryptocurrency space, to protect against nation-state actors seeking to exploit vulnerabilities for financial gain and support illicit programs.
3. Lack of Cybersecurity Priority? Few Fortune 100 Companies Include CISOs in Top Executives.
A new piece from Brian Krebs highlights how Fortune 100 companies are falling short in prioritizing cybersecurity within their executive ranks, as revealed in a recent analysis. Despite the critical role of security professionals in safeguarding customer data and privacy, only four out of the Fortune 100 firms currently list a Chief Security Officer (CSO) or Chief Information Security Officer (CISO) among their top executives.
This number is even lower than in 2018 when five companies included security professionals in their leadership pages. The analysis also showed that a significant number of companies listed Chief Technology Officers (CTO) and Chief Information Officers (CIO) but overlooked the importance of Chief Risk Officers (CRO) and security personnel.
The absence of CSOs or CISOs from the highest echelons (see what I did there?) of companies may be attributed to reporting structures, with these security leaders often not directly reporting to the CEO, board of directors, or CRO. Experts argue that this unequal footing hinders cybersecurity and risk concerns from receiving the attention they deserve, as they may be overshadowed by initiatives focused on productivity and business growth. Moreover, security leaders often lack the legal and insurance protections afforded to other top executives, which further diminishes their prominence in corporate executive biographies.
The article calls out surveys conducted by IANS and Datos Insights, which confirm that a majority of CISOs and CSOs report to technical leaders, such as the CTO or CIO. This trend is consistent across industries and has seen little change over the years. A recent Accenture study found that only a third of organizations surveyed have integrated security into various aspects of their businesses, and cybersecurity risk is not fully considered when evaluating overall enterprise risk. The data underscores the need for organizations to prioritize cybersecurity at the executive level and ensure adequate legal protections for their security leaders.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
