Cyber Intelligence Weekly (July 24, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major
developments on the future of cybersecurity that you need to know about.
Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight an upcoming webinar we have with our friends at PlexTrac this week! We are going to speaking about different maturity levels within the realm of offensive security and how to achieve higher heights, please sign up here and join us!

Away we go!
1. Data of 5.4 Million Twitter Users is Allegedly up for Sale
A new report from Bleeping Computer outlines a potential data breach at social media giant Twitter. A hacker named “devil” has posted that they are selling the data on over 5.4 million Twitter users on a dark web forum, Breached Forums, for $30,000.
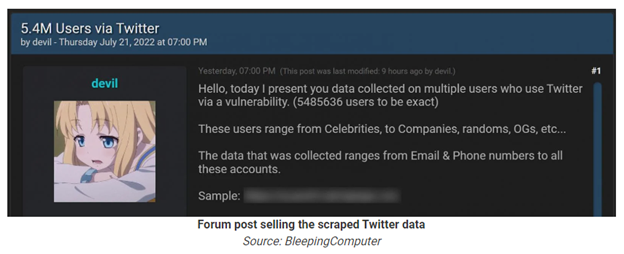
The hacker apparently was able to scrape this data from an old Twitter vulnerability that was reported back in January of this past year. Per the Hacker One report, “The vulnerability allows any party without any authentication to obtain a twitter ID (which is almost equal to getting the username of an account) of any user by submitting a phone number/email even though the user has prohibited this action in the privacy settings. The bug exists due to the process of authorization used in the Android Client of Twitter, specifically in the process of checking the duplication of a Twitter account.”
It is being reported that samples of the Twitter data appear to be legitimate thus far. As of the time of this writing, Twitter has not confirmed a data breach. This will be an interesting one to track.
2. Popular NFT Queue Software PREMINT Compromised, $375k in NFT’s Stolen
PREMINT, one of the top NFT services that allows artists to build access lists and randomly select collectors to enter NFT drops, announced a data breach last week that allowed hackers to take over accounts and steal NFTs.
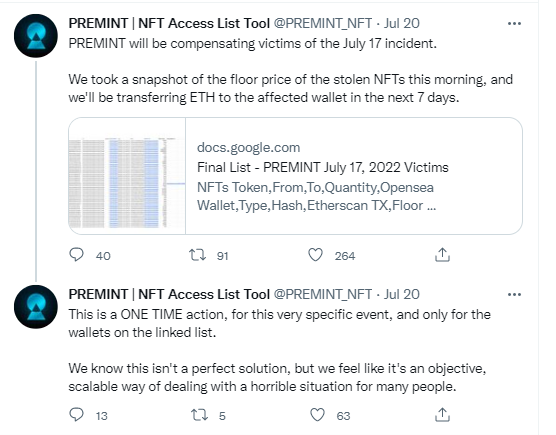
Per the PREMINT blog entry on the security incident, the threat actors leveraged a vulnerability in an open-source image uploader tool to evade upload restrictions. As a result, the attacker was allowed to write uploaded files to destinations outside the specified directories in an AWS S3 bucket. The attacker then launched the attack by serving malicious JavaScript to the storage location. The malicious JavaScript rewrote parts of the PREMINT login and their “Connect Wallet” dialog. Affected users would then see a popup asking them to verify their wallet ownership, users who fell for this prompt agreed to a "SetApprovalForAll" setting in their wallet, which allowed the hackers to steal their wallet contents.
This incident shows the damage that client-side JavaScript can have when presented to unsuspecting end users. While the internal databases of PREMINT weren’t accessed or affected in any way, a ton of damage was done by tricking a handful of users to allowing the hackers to access their accounts.
3. Russian Hackers Released Fake Pro-Ukrainian App to Track Users and Infrastructure
Google’s Threat Analysis Group (TAG) put out some new research recently based on the tracking and intelligence gathering they been performing in Eastern Europe with regard to the war in Ukraine. They’ve been tracking the operations and movements of several Russian backed threat actor groups for some time.
Most recently, Google’s TAG put the spotlight on Russia’s “Turla” group, a group that has been publicly attributed to Russia’s Federal Security Service, our equivalent of the FBI. CrowdStrike dubs this threat actor as “Venomous Bear.” Per CrowdStrike’s description of this group, “Venomous Bear is a Russia-nexus adversary that often adopts novel and sophisticated techniques to maintain operational security, including the use of a distinctive command-and-control network highly likely to be supported by Signals Intelligence assets. Operations conducted by VENOMOUS BEAR characterize them as a highly motivated, espionage-focused adversary who aims to obtain diplomatic intelligence, likely to inform reporting to different levels of the Russian government.”

Photo Source: CrowdStrike
Per the Google TAG threat intel, the Turla group recently hosted the Android app on a domain spoofing (cyberazov[dot]com) the Azov Regiment, a unit of the National Guard of Ukraine. The app claimed to be able to perform a denial-of-service attack against Russian targets at the user’s behest. The app actually didn’t really do anything of the sort, rather, it was designed to track the users and infrastructure of people who would want to use such an app against Russia.
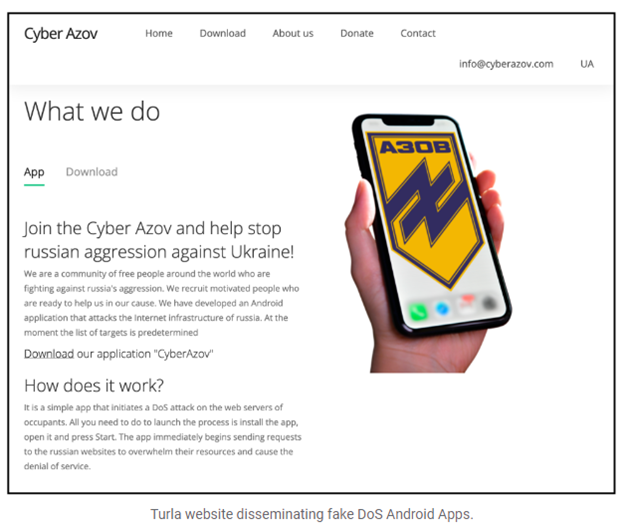
Photo Source: Google
Per Google’s TAG, the app never made it to the Google Play Store, but it was disseminated through fake links and messaging programs. They do not believe that there was any major impact from these events and a very small amount of users actually downloaded the fake app. This story still highlights the lengths that a determined enemy will go in the midst of a hybrid kinetic/cyber war.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
