Cyber Intelligence Weekly (January 14, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight that we recently sat down to refresh and evolve our values, and we could not be more happy with where we landed. Now we want to share the evolution with you, and explain more about how we fine-tuned our values to go beyond the basics and embody our active pursuit of excellence.
One of our old values, "Integrity," is now considered a baseline expectation for our firm. The updated version focuses on the ethos of "Turning Pro," which is something we always strive for – transcending the ordinary, embracing challenges, and fostering a culture of continuous improvement.
Ready to embark on this journey with us? Visit our website to read about our updated core values! https://lnkd.in/eEpydrmu

Away we go!
1. AI in Cybersecurity: A Double-Edged Sword
In a recent conference at Fordham University, Rob Joyce, the Director of Cybersecurity at the U.S. National Security Agency (NSA), discussed the evolving landscape of cyber threats and the role of artificial intelligence (AI) in both aiding hackers and bolstering U.S. defenses. Joyce highlighted how both criminal and nation-state actors are increasingly utilizing generative AI models for cyberattacks. These attackers are leveraging AI to enhance their hacking capabilities, making them more effective and dangerous. This use of AI is not limited to sophisticated actors; it's also enabling less capable individuals to improve their technical hacking skills.
Joyce pointed out that the same AI technologies being exploited by these malicious actors are also proving beneficial for U.S. intelligence. AI, machine learning, and deep learning are significantly improving the NSA's ability to detect and counteract malicious activities. By analyzing patterns and behaviors that deviate from the norm, these technologies help identify unauthorized activities, even when attackers disguise their presence within networks.
The NSA director also highlighted recent cyber activities by China-backed hackers targeting U.S. critical infrastructure. These attacks, which aim to disrupt societal functions, don't rely on traditional malware but exploit vulnerabilities to gain network access, appearing as legitimate users. AI technologies are instrumental in surfacing these activities by distinguishing between normal operations and suspicious behaviors.
Joyce's comments come amidst a broader discussion on the use of generative AI tools in cyberattacks and espionage, as well as efforts by the Biden administration to establish standards for AI safety and security. Other government agencies have also warned about the potential misuse of AI in scams and fraud. Despite the challenges, Joyce's insights underscore the dual role of AI as both a tool for cybercriminals and a key asset in cybersecurity defenses.
2. Bitcoin ETF Fake News, The SEC X (Twitter) Account Compromise
The U.S. Securities and Exchange Commission (SEC) recently faced a significant security breach when its official SECGov X (Twitter) account was compromised. This led to the unauthorized posting of false information about Bitcoin ETFs, which are financial products allowing investment in Bitcoin like standard stocks. The fake post, which included a bogus quote from SEC Chair Gary Gensler, was quickly removed, but not before causing a temporary fluctuation in Bitcoin's value. The SEC has since confirmed that the breach resulted from an unknown individual gaining control over a phone number associated with the account, rather than a system failure on Twitter's part.
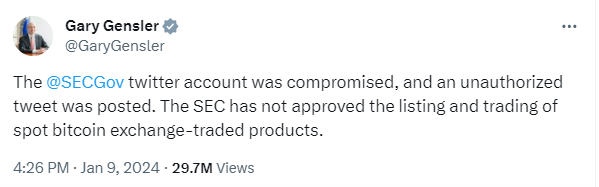
The incident has raised concerns about the security of high-profile Twitter accounts, especially in the wake of recent staff reductions by Twitter owner Elon Musk. Critics, including U.S. Senator Bill Hagerty, have called for an investigation into the breach, drawing parallels to the demands the SEC would make of a public company in a similar situation. This breach is not an isolated incident; another recent high-profile Twitter account hack targeted Mandiant, a cybersecurity firm. The hack involved posting a malicious link to steal cryptocurrency.
The SEC's account compromise is seen as one of the most significant since the 2020 incident where hackers gained access to Twitter's internal tools, enabling them to control high-profile accounts including those of Joe Biden, Barack Obama, and Elon Musk. The incident underscores ongoing concerns about Twitter's ability to secure its platform against such attacks, especially considering past whistleblower reports about security issues at Twitter. As a response to the latest breach, Musk humorously replied to a tweet about the SEC's password, highlighting the ongoing challenges of ensuring the security of influential social media accounts.
3. Vulnerabilities Exposed in AI Hiring Chatbot by Hackers, Exposing Personal Data
Continuing on the AI theme, a recent cybersecurity incident revealed a significant vulnerability in an AI chatbot, Chattr, used by fast food franchises for automating hiring processes. In this exclusive story from 404 Media, Joseph Cox reported that hackers, including a researcher known as MrBruh, successfully infiltrated the backend of Chattr, gaining access to sensitive data including applicant information and internal operations of the franchises. The breach was initially discovered by MrBruh, who used a script to scan for exposed Firebase credentials, commonly used by app developers. The script identified a Firebase configuration related to a KFC franchise, leading to further exploration using a security testing tool, Firepwn.
Upon creating a new user account, the researchers gained extensive access to the database, uncovering names, contact details, work shifts, and even some passwords. This breach extended beyond just KFC, as the researchers were able to access an administrator dashboard showing a list of organizations using Chattr. This access granted them the ability to accept or reject job applications and refund payments made to Chattr. In a detailed video and blog post, MrBruh and another researcher, Eva, demonstrated the ease with which they could navigate the Chattr backend, accessing data from various organizations, including Chick-fil-A and Subway.
The seriousness of the breach was underscored by the potential to ransom the data, as mentioned by MrBruh. However, after reporting the issue to Chattr, it was resolved within a day, albeit without acknowledgment or thanks from Chattr. KFC clarified that Chattr was affiliated with only one of its franchisees and not directly with KFC Corporation. This incident highlights significant security concerns in the rush to implement AI solutions in business operations, especially regarding the safeguarding of sensitive personal and corporate data.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
