Cyber Intelligence Weekly (January 28, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight the top articles from 2023 that our team authored on Echelon’s Intelligence Blog:
Away we go!
1. More Details Revealed on the Midnight Blizzard Attack on Microsoft
Microsoft's security team dropped some heavily anticipated new details on the January 12th attack on its corporate systems by a nation-state threat actor. The threat actor, identified as Midnight Blizzard, a Russian state-sponsored actor also known as NOBELIUM, targeted Microsoft through sophisticated methods. The Microsoft Threat Intelligence team's investigation revealed the intricate techniques used by Midnight Blizzard and provided insights on how organizations can protect, detect, and respond to similar threats. The Microsoft Security and Response Center (MSRC) has published the latest information on this incident.
Midnight Blizzard, known for targeting governments, NGOs, and IT service providers primarily in the US and Europe, employs various techniques for espionage and intelligence gathering. They use diverse methods for initial access, such as stolen credentials and supply chain attacks, and are skilled in compromising authentication mechanisms to expand access and evade detection. In this particular attack, Midnight Blizzard used a password spray attack to compromise a non-production test tenant account at Microsoft, which lacked multifactor authentication (MFA). The attackers then created and misused OAuth applications to maintain access within Microsoft's environment and to gather intelligence. Unfortunately, by default, any user can create app registrations and consent to Graph permissions as well as sharing 3rd party company data. Note, it is highly recommended that you do not allow user consent to apps automatically.
Uncheck this box to change this insecure default:
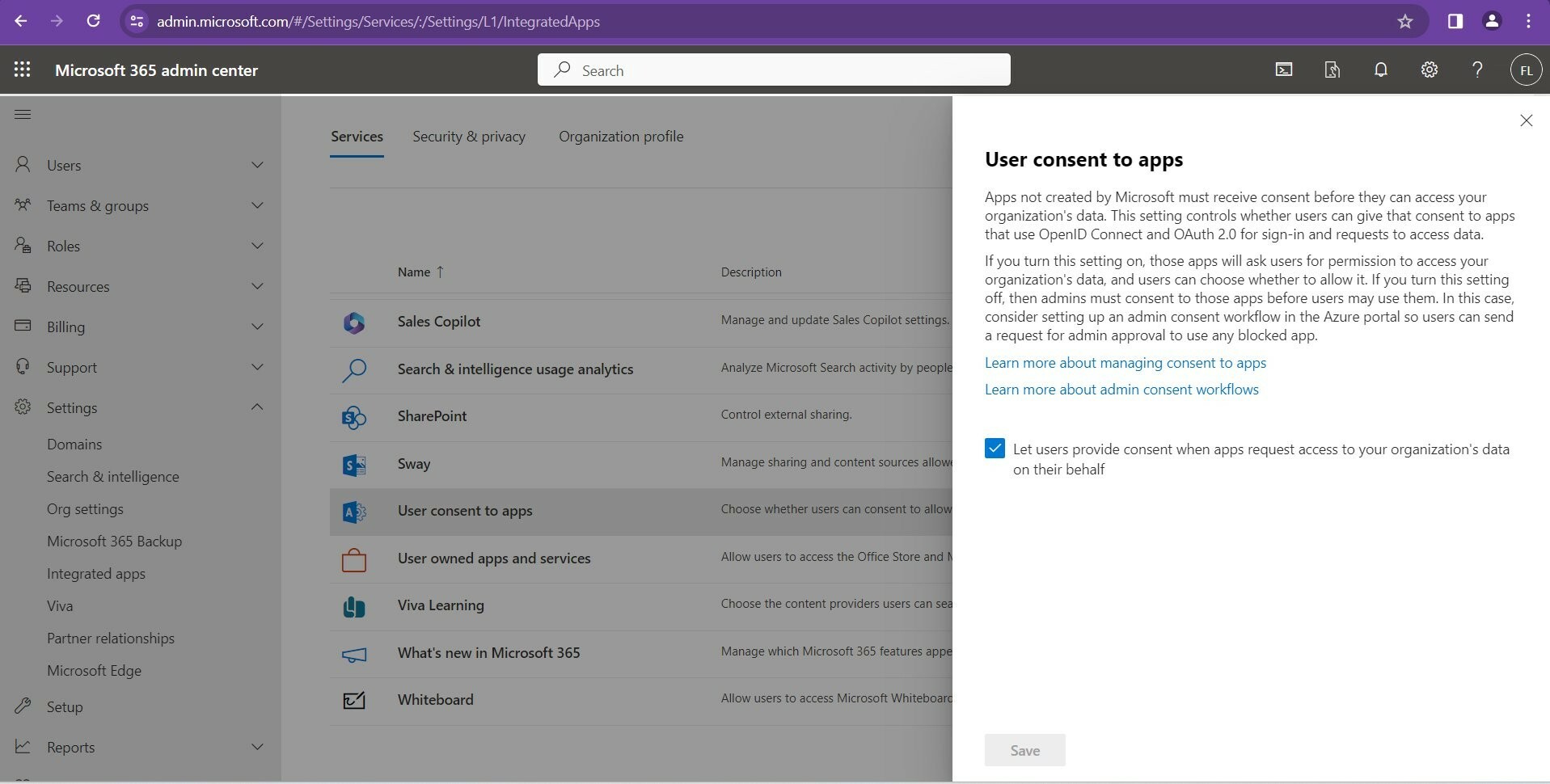
The attack also involved sophisticated methods like using residential proxy networks to mask the source of the attack, making traditional detection methods based on indicators of compromise ineffective. Microsoft was able to detect these activities by analyzing Exchange Web Services (EWS) and leveraging audit logging features, combined with their deep knowledge of Midnight Blizzard’s tactics. This ongoing investigation highlights the need for advanced security measures and the importance of swift and comprehensive response strategies in the face of state-sponsored cyberattacks.
Microsoft provided a full list of defense and protection guidance to thwart these types of attacks, here is a quick summary:
- Audit all user and service principal identities in your tenant using Microsoft Graph Data Connect to assess their privilege levels. Scrutinize privileges more closely if they belong to unknown identities, are no longer in use, or exceed necessary levels, especially for apps with app-only permissions that might have over-privileged access.
- Review identities with ApplicationImpersonation privileges in Exchange Online. This feature allows a service principal to perform actions on behalf of a user, like managing a mailbox. Check permissions in the Exchange Online Admin Center or via PowerShell to ensure they are appropriately scoped and not overly broad.
- Utilize anomaly detection policies to identify and address malicious OAuth apps in Exchange Online. Investigate and remediate any risky OAuth apps that perform sensitive administrative activities.
- Implement conditional access app control for users on unmanaged devices. Be vigilant of OAuth application abuse, particularly those with EWS.AccessAsUser.All and EWS.full_access_as_app permissions, and remove any unnecessary permissions.
- For applications requiring mailbox access, use role-based access control in Exchange Online to ensure granular and scalable access. This model allows applications to access only the specific mailboxes they need, enhancing security.
2. Before Microsoft, Tracing Midnight Blizzard’s Attack on HPE
Months before the high-profile Microsoft breach, the same threat actor had already infiltrated Hewlett-Packard Enterprise (HPE). According to a recent Form 8-K SEC filing, HPE disclosed that Midnight Blizzard, also known as Nobelium, Cozy Bear, and APT29, breached its cloud-hosted email system in May 2023. During this breach, the attackers exfiltrated data from the email accounts of a select group of individuals across various departments, including cybersecurity, marketing, and business.
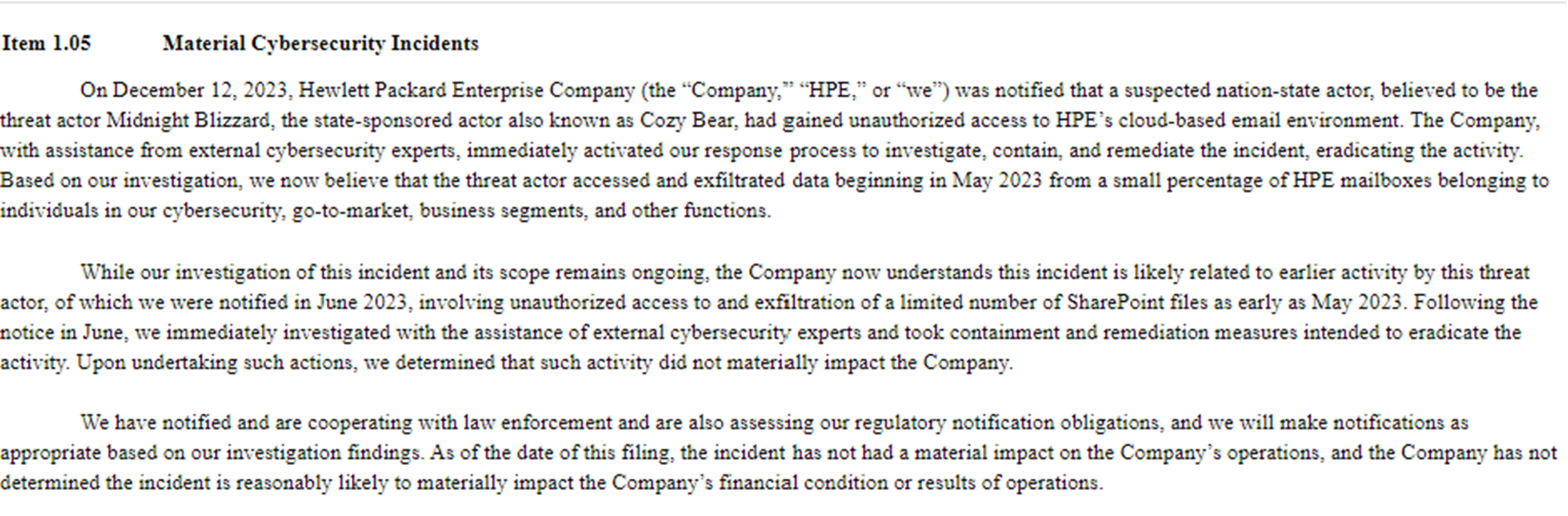
HPE discovered the breach on December 12, 2023, and has since been collaborating with external cybersecurity experts to assess the full impact and timeline of the intrusion. The company's investigation revealed that this incident was likely part of a series of activities by Midnight Blizzard, dating back to May 2023. This earlier activity involved unauthorized access and exfiltration of a limited number of files from HPE's SharePoint. These revelations not only underscore the sophistication and persistence of Midnight Blizzard but also highlight the ongoing cybersecurity challenges faced by major corporations.
This breach at HPE serves as a precursor to the later, more widely reported attack on Microsoft, indicating a pattern of targeted attacks by Midnight Blizzard against significant technology companies. The group's focus on accessing and extracting sensitive information from top-level corporate entities emphasizes the critical need for enhanced security measures and information sharing against such advanced threat actors.
3. Australia Imposes First-Ever Cyber Sanctions on Russian Hacker Behind Medibank Breach
The Australian government has made a significant move by imposing sanctions against Russian national Aleksandr Ermakov, identified as the perpetrator of the Medibank Private data breach. This action marks the first use of the country's cyber sanctions framework, established in 2021, which allows for financial punishments against individuals involved in major cyber attacks.
The Medibank breach, which occurred in 2022, resulted in the theft of personal information of 9.7 million customers, including sensitive data such as names, dates of birth, Medicare numbers, and private health details. A substantial portion of this stolen data was later published on the dark web. The Australian Signals Directorate and the Australian Federal Police identified Ermakov as the individual responsible for this cyber attack. Under the new sanctions, it is now a criminal offense to provide Ermakov with any assets, including cryptocurrencies and ransom payments, with violations carrying penalties of up to 10 years in prison.
Home Affairs Minister Claire O'Neil described the Medibank incident as the most devastating cyber attack Australia has experienced, emphasizing the personal impact on millions of people whose data was maliciously exposed online. The government's actions are a clear statement against such cybercrimes, underscoring their commitment to identifying and holding responsible parties accountable. The investigation into the Medibank attack continues, with Australian authorities focusing on various Russian cyber gangs and collaborating with cyber authorities in the US and UK. Medibank has expressed gratitude for the government's efforts in identifying Ermakov and enforcing sanctions.
Additionally, Foreign Minister Penny Wong announced counter-terrorism sanctions against individuals and entities linked to Hamas, Hezbollah, and Palestinian Islamic Jihad. The opposition, while welcoming the cyber sanctions and acknowledging the efforts of law enforcement, criticized the government for not acting sooner, both in the cyber attack and counter-terrorism contexts.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about

