Cyber Intelligence Weekly (June 4, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight an upcoming webinar with Echelon and our friends at Panorays. How is third-party risk like a blind date? Join this upcoming webinar, "Vendor Security Risk: A Blind Date Encounter," on June 13 to find out! Discover the intriguing parallels between onboarding a new vendor and going on a blind date. Just like in a budding relationship, first impressions matter! Gain invaluable insights on what to look for (and what to avoid) when selecting a vendor, how to foster trust, and the keys to maintaining a mutually beneficial partnership in the long term.
Our esteemed speakers, Dov Goldman - VP of Risk Strategy at Panorays, and Tom Garrubba - Director of TPRM Services at Echelon Risk + Cyber, will share their expertise in risk analysis, due diligence, and the significance of comprehensive assessments for establishing successful vendor relationships. Don't miss this opportunity to acquire practical strategies that will help you navigate the vendor landscape with confidence! Register now for an engaging and informative session that will transform the way you approach vendor onboarding and risk mitigation here: https://lnkd.in/d62NKs5g

Away we go!
1. MOVEit, Get out the Way, Get out the Way!
Progress Software Corp. has issued a warning about a critical vulnerability in its widely used file-transfer software, MOVEit, which exposes customers' networks to unauthorized access by malicious actors. The security flaw has already been exploited by hackers, with several companies and cybersecurity investigators currently investigating cases related to the exploitation. MOVEit and similar file-transfer tools have become attractive targets for ransomware groups and cybercriminal organizations in recent years. Organizations that utilize these tools should be prepared for potential data extortion and theft, as hackers exploit the vulnerability. Progress has released fixes for the affected versions and advises customers to disable web traffic to the program until the patches are applied.
Upon exploiting the vulnerability, the threat actors leverage a newly discovered web shell, dubbed “LEMURLOOT” by Mandiant, to interact with the compromised MOVEit Transfer platform. The web shell is deployed with filenames that masquerade as “human.aspx”, which is a legitimate component of the MOVEit Transfer software. The malware authenticates incoming connections using a hard-coded password and enables the execution of commands for various malicious purposes. By manipulating HTTP header fields, such as X-siLock-Step1, X-siLock-Step2, and X-siLock-Step3, LEMURLOOT performs actions like retrieving Azure Blob system settings, extracting file and folder information, and even creating or deleting user accounts.
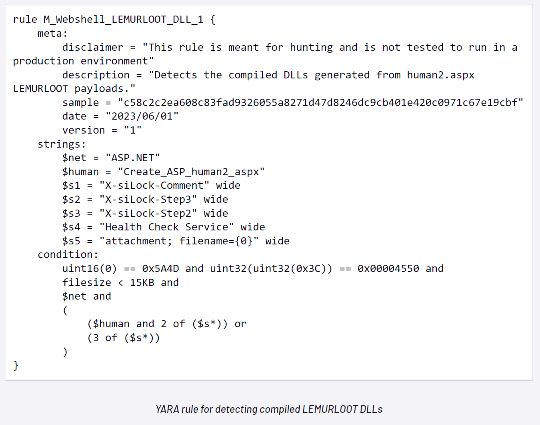
Patches for the affected MOVEit software are available through the website of Progress, additionally several firms have been releasing detections. Such as the YARA rules and known hashes, see more from Mandiant in their blog here.
2. Barracuda Discloses Seven-Month Exploitation of Zero-Day Vulnerability
What do you call two barracuda fish? A Pairacuda! This week, we have another significant product based vulnerability, this time in the Barracuda software and appliances.
Barracuda, a network and email security firm, has disclosed that a zero-day vulnerability, known as CVE-2023-2868, was exploited for seven months to install custom malware and steal data from customers' Email Security Gateway (ESG) appliances. The attackers gained access to a subset of ESG appliances in October 2022 and deployed backdoors to maintain persistent access to the compromised systems. Barracuda discovered evidence of data theft from the compromised appliances. The security flaw was identified on May 19, and Barracuda promptly addressed it by applying a security patch and blocking the attackers' access. The company has warned customers about the breach and is deploying security patches to all affected appliances as part of its containment strategy. Custom-tailored malware strains, dubbed Saltwater and SeaSpy, were used in the attack to establish backdoor access and provide persistence on the compromised devices. Detailed mitigation advice, network IOCs, endpoint IOCs and YARA rules have been posted on the Barracuda blog related to this issue.
The Cybersecurity and Infrastructure Security Agency (CISA) has added the CVE-2023-2868 vulnerability to its list of known exploited vulnerabilities, indicating a potential risk to federal agencies using ESG appliances. Barracuda has advised customers to ensure their ESG appliances are up-to-date, stop using compromised appliances, rotate all credentials associated with the affected devices, and review network logs for indicators of compromise (IOCs) shared by the company.
3. FTC Takes Aim at Amazon: Alexa and Ring Settlements Highlight Privacy Concerns
Amazon has agreed to pay a $25 million settlement to resolve a lawsuit filed by the Federal Trade Commission (FTC) over privacy concerns related to its voice assistant, Alexa, and its handling of children's data. The FTC alleged that Amazon violated both the FTC Act and the Children's Online Privacy Protection Act (COPPA) by retaining children's voice recordings and transcripts for longer than allowed. The company kept this data indefinitely until September 2019, failing to delete it in a timely manner as required.

In response to the settlement, Amazon stated its disagreement with the FTC's claims but decided to settle the matter to move forward. The company asserted that it designed Amazon Kids with COPPA compliance in mind and provided parents with easy ways to delete recordings and transcripts. Additionally, Amazon committed to deleting child profiles that had been inactive for at least 18 months to address concerns about data retention.
This settlement comes alongside another agreement between the FTC and Amazon-owned Ring, in which Ring settled allegations of privacy violations. The FTC claimed that Ring allowed employees and contractors full access to customer video content, leading to privacy breaches.
Despite these settlements, it is clear that the FTC intends to keep a close eye on Amazon and other tech giants, as the penalties imposed may not be substantial but demonstrate the regulator's commitment to ensuring compliance within the industry.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about

