Cyber Intelligence Weekly (September 3, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight the fact that Echelon is a preferred provider of Cybersecurity Tabletop Exercises. A well-prepared team can be your strongest defense against cyber threats. Just as fire drills train us for emergencies, cybersecurity tabletop exercises prepare our teams for potential cyber threats. Dive into this practice and discover how it can bolster your cyber resilience! Reach out to me today to schedule a free consultation about how we can help your company with a tabletop experience today!

Away we go!
1. MTA's "Feature" Raises Serious Privacy Concerns
A recent investigative report from Joseph Cox at 404 has highlighted alarming privacy vulnerabilities in the Metropolitan Transportation Authority (MTA) website’s OMNY contactless payment system. Without any physical proximity, an individual could track the subway movements of a New York City rider. By merely inputting the rider's credit card information, which can often be acquired illicitly or simply known by close acquaintances, they were able to access the rider's 7-day travel history. This occurred without any additional verification, exploiting a feature ostensibly created for users to view their own travel history.
The revelation underscores a significant potential for misuse, particularly by abusive partners or other malicious actors. Notably, while the MTA does offer a secure version of the trip history feature, which requires account authentication, the site defaults to the unauthenticated version. In the article, Eva Galperin of the Electronic Frontier Foundation criticized the system’s lax security, pointing out that a simple PIN or password addition would curtail such privacy risks. Furthermore, while the MTA emphasizes that OMNY only logs entry points and doesn't reveal real credit card numbers, concerns remain about the system’s potential misuse by anyone possessing a person's payment details. Credit card numbers are easy to get these days based on all the recent data breaches.
The OMNY system has previously come under scrutiny, with advocacy groups like the Surveillance Technology Oversight Project (STOP) expressing concerns about its data collection and potential sharing with law enforcement. Such systems, they argue, have historically been misused by agencies to target minorities. In response to the revelations and subsequent media attention, the MTA announced plans to disable the contentious feature, signaling a move towards addressing these privacy concerns. We can confirm that this feature has since been disabled and has been replaced with the following statement, “This feature has been removed while we evaluate new tools to serve our customers who choose not to create an OMNY account.”
2. Duolingo User Data Leak Raises Concerns on Data Scraping
Duolingo has announced that it is investigating a claim of data scraped from its app for approximately 2.6 million Duolingo users that was made available on a hacking forum, setting the stage for potential targeted phishing attacks using the stolen data. Duolingo, a prominent language learning platform with a user base of over 74 million monthly users globally, found itself in the spotlight when a hacker offered the scraped data of these users for $1,500 on the now-defunct Breached hacking forum. This data bundle not only consisted of publicly accessible login and real names but also contained non-public information such as email addresses and other internal details pertaining to the Duolingo service.
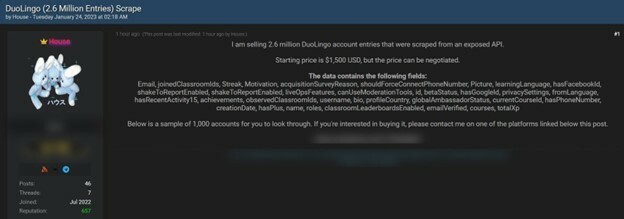
The data set was subsequently spotted on a revived version of the Breached hacking forum. This public availability of data is attributed to an exposed Duolingo API that had been openly shared since March 2023. Using this API, one could enter a username and obtain related public profile details. What's more concerning is that entering an email address would verify if it is linked to an active Duolingo account. By leveraging this API, the scraper correlated email addresses from past breaches with Duolingo accounts to compile a dataset that meshed public and private information. Here is a blog where security researchers showed how to use (and potentially abuse) this data.
Despite companies often downplaying the risks associated with scraped data since much of it is public, the combination of public and private data (e.g., email addresses or phone numbers) elevates the potential risks. This blending can also contravene data protection regulations. For instance, in 2021, Facebook faced a hefty €265 million ($275.5 million) fine after an API bug led to the exposure of phone numbers linked to 533 million accounts. Similarly, Twitter is under scrutiny for a recent API flaw that exposed user data.
3. U.S. Takes Down QakBot Botnet in Major Operation
In a monumental international operation named "Duck Hunt," the U.S. Department of Justice (DOJ) and Federal Bureau of Investigation (FBI) took substantial measures against QakBot, a sophisticated malware responsible for laying the groundwork for numerous ransomware infections. The U.S. government coordinated efforts to seize the botnet's infrastructure and discreetly eliminated the QakBot malware from a vast number of infected Microsoft Windows systems. Martin Estrada, the U.S. attorney for the Southern District of California, declared this the most impactful technological and financial action against a botnet to date, emphasizing QakBot's role in 40 different ransomware attacks in the last year and a half, resulting in over $58 million in victim losses.
Tracing its roots back to 2007 as a banking trojan, QakBot (also known as Qbot or Pinkslipbot) has since evolved into a potent malware used by several cybercriminal factions to ready compromised systems for ransomware deployments, primarily disseminated via deceptive email phishing campaigns. Don Alway, of the FBI’s Los Angeles branch, shared that investigators accessed an online panel giving cybercriminals the power to oversee and manipulate the botnet. This access allowed them to obtain legal authorization to command infected devices to uninstall QakBot and disengage from the botnet. Astonishingly, in the past year alone, QakBot infected over 700,000 devices, with 200,000 being in the U.S.
Collaborating with multiple international law enforcement agencies, the DOJ managed to confiscate more than 50 servers associated with the malware network and seized nearly $9 million in cryptocurrency from the masterminds behind QakBot. This isn't the first instance of the U.S. using court orders to remotely cleanse malware-infested systems. In a similar effort, the DOJ neutralized the "Snake" malware in May 2023. As a part of the current operation, the DOJ also retrieved over 6.5 million purloined passwords and credentials, now made accessible for users to verify their exposure on platforms like "Have I Been Pwned" and the "Check Your Hack" website.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
