Cyber Intelligence Weekly (October 15, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight that we're back with another episode of our "Chew on This" webinar series, and you won't want to miss it! 🚀
📅 Save the Date: Wednesday, November 1st
🕛 Time: 1:00 PM ET
🎙️ Panelists: Matt Donato and Paul Interval
🌟 Potential Guest: Stay tuned for updates!
This episode will delve deep into the vital relationship between a Virtual Chief Information Security Officer (vCISO) and a Chief Information Officer (CIO) in the realms of cybersecurity and overall business strategy.
This collaboration fortifies the organization's cybersecurity framework and bolsters its long-term success. We've designed this webinar especially for IT Executives and Leaders in medium-sized, growing businesses.
Mark your calendar and get ready to boost your cybersecurity and business strategy knowledge. We can't wait to see you there! 🤝💡
Link to register: https://www.linkedin.com/events/cios-chewonthis-shouldavcisobet7118338556552466432/theater/

Away we go!
1. Cyber Chaos: How Hacktivists Intensify the Israel-Hamas Conflict
In the wake of escalating conflict between Israel and Hamas, hacktivists from around the world have rushed to join the digital battleground, targeting both Israeli and Palestinian websites and applications. These hacktivists have launched a series of attacks, including defacements, Distributed Denial of Service (DDoS) attacks, and attempts to overload targets with excessive traffic, with the aim of disrupting services and spreading their messages. Some groups have also claimed to have stolen data and attacked internet service providers.
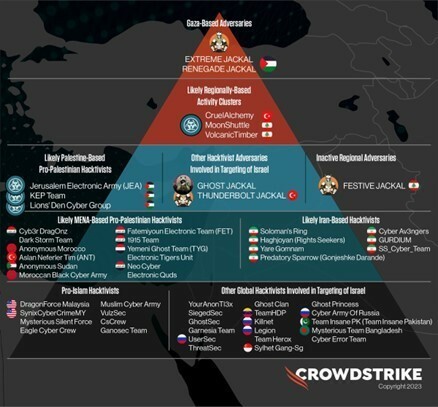
The hacktivist activities can be typically be categorized into three subsets within the Israel-Hamas conflict. First, there are self-proclaimed "Islamic" hacktivists supporting Palestine, who have historically targeted India and have been active for years. Second, there are pro-Russian hacktivists pivoting to target Israel, potentially to sow chaos and promote Russian state narratives. Lastly, there are newly-formed groups that have emerged recently and have limited prior activities. These groups have jumped into the conflict, aligning with various geopolitical interests.
Hacktivist activities in conflicts like this often fuel disinformation and panic, contributing to the overall chaos. However, experts suggest that while hacktivism may exacerbate the turmoil, it is unlikely to significantly impact the warfare on the ground. The International Committee of the Red Cross has released rules of engagement for "civilian hackers" participating in conflicts, emphasizing the importance of minimizing threats to civilian safety and banning cyberattacks on healthcare facilities. These rules aim to provide some ethical guidelines in this increasingly complex digital landscape.
Hacktivism has become a stark reality of modern conflicts, with various groups and individuals participating to advance their agendas. The digital battlefield is nuanced and unpredictable, and while hacktivism may create chaos and disinformation, its impact on the overall conflict remains limited. This trend underscores the importance of addressing the role of hacktivism in modern warfare and establishing ethical guidelines to minimize harm to civilians.
2. Vietnamese Government's Bold Attempt to Hack U.S. Officials
The Washington Post recently revealed a story claiming that Vietnamese government agents attempted to hack the phones of U.S. officials, including members of Congress, policy experts, and journalists in a bold campaign that employed advanced hacking tools. The hackers used Twitter, referred to as X in the article, to distribute links designed to install the Predator spyware on target devices.
Predator is a potent surveillance program capable of activating microphones, cameras, retrieving files, and reading encrypted messages on smartphones. Although the hacking attempts appear to have been unsuccessful, they occurred while the U.S. and Vietnam were negotiating a significant cooperation agreement to counter growing Chinese influence in the region.
The investigation suggests that Predator was sold from the European company Intellexa, which was added to the U.S. Commerce Department's Entity List in July 2023, to the Vietnamese Ministry of Public Security through various intermediaries. While the victims reported not clicking on the links, the hacking campaign was surprisingly public, with an anonymous Twitter account posting links in replies to the targets' tweets.
The use of such spyware highlights the urgent need for stronger oversight and regulation of the spyware industry. As a response, bills are being considered in various countries to regulate the industry as rampant misuse and abuse of spyware tools have been exposed globally.
3. Robinhood Users Beware: Hackers Exploit Accounts in Cash-Out Scams
In a concerning development, hackers are actively targeting Robinhood accounts, the popular online brokerage platform, with the aim of stealing customer funds. A comprehensive review of criminal forums and Telegram groups conducted by 404 Media has shed light on the illicit activities surrounding these attacks. They reported that hackers have been seen advertising compromised Robinhood accounts for sale as part of their nefarious operations.
This criminal ecosystem involves various players offering specialized services, from acquiring email addresses and passwords to developers creating tools to intercept multi-factor authentication codes. On fraud-focused Telegram groups, messages like "Send me all yo Robinhoods. Instant cashout" and "cashing all Robinhoods rn" are common, reflecting their sinister intent. Some fraudsters are selling "FA" (full access) Robinhood accounts for as little as $2 or $3, claiming access to over a hundred such accounts. These accounts may have been obtained through techniques like using configuration files to exploit reused passwords.
Furthermore, hackers are exploiting the Robinhood feature that allows cryptocurrency trading, making such accounts particularly attractive targets. Criminal communities are also offering services to cash out the compromised accounts, with some fraudsters charging a cut of 15 to 50 percent depending on the account balance. These actors are equipped with sophisticated tools, including one-time password bots that can circumvent Robinhood's security measures. The situation raises concerns about the security of online financial accounts that target unsuspecting consumers and underscores the importance of robust cybersecurity practices for both individuals and platforms like Robinhood.
PS: I’ve been really impressed with the reporting from Joseph Cox at his new 404 Media venture, please check him out and support him!
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
