A complete team of cybersecurity pros, delivered as-a-service, led by an experienced vCISO
Cybersecurity is a team sport - don’t try and tackle it alone. Our whole-team approach advances cybersecurity posture and minimizes organizational risk.

Cybersecurity is a team sport - don’t try and tackle it alone. Our whole-team approach advances cybersecurity posture and minimizes organizational risk.

The Security Team as a Service (STaaS), led by a Virtual Chief Information Security Officer (vCISO), is your business's strategic advantage in the digital world.
Think of it as having a security expert on speed-dial, along with their team of cyber specialists, ready to protect your business from all threat actors.
The security team helps ensure that your company's systems, data, and people are well-protected, while also making sure you tick all the right boxes when it comes to legal and industry standards for cybersecurity.
Strategic and Tactical Partnership - more than just a vCISO, you get a team that acts as an extension of your business, tailored to your business
Full Support from a Virtual Security Team - access to Offensive Security Consulting + Adversarial Simulation, Defensive Security Consulting + Hardening, and Cyber Risk Advisory + Compliance capabilities
Industry Experts, in Your Corner - we’ve got your back
Freedom to Focus - you focus on running your business while we advance your cybersecurity initiatives
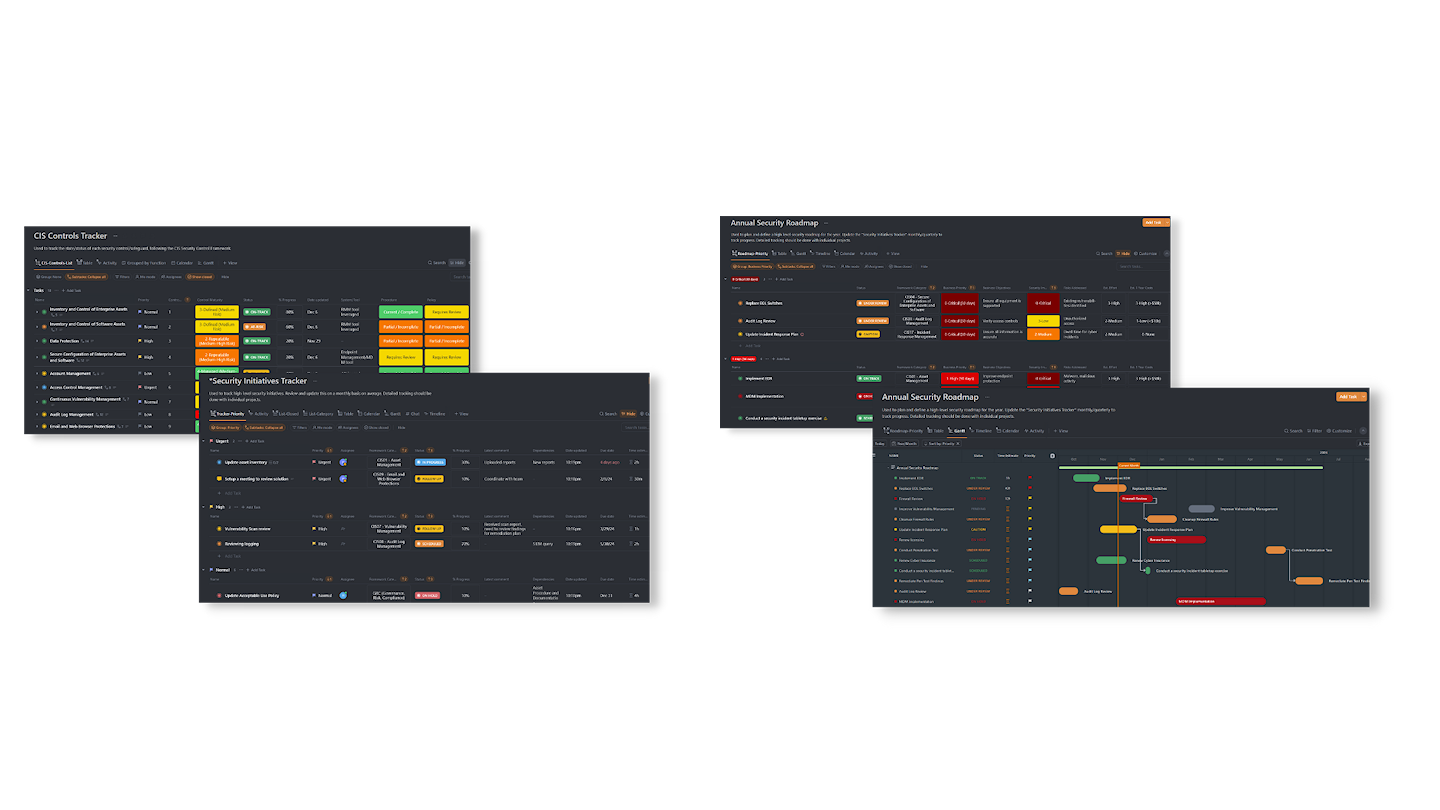
All our packages include our Cybersecurity Management Portal, a web-based portal where our client’s teams can collaborate directly with their Echelon Cybersecurity Team.
All projects, tasks and initiatives are tracked within the portal to give you real-time progress updates.
The portal is a repository for all the cybersecurity program information, including inventories, policies, and documentation.
All strategy meetings and workshops are tracked in the portal, including notes with key takeaways and next steps to keep everyone aligned.
Our Security Team as a Service is led by a Virtual Chief Information Security Officer (vCISO) to help mature your cyber strategy and oversee your cybersecurity efforts. This unique combination is designed to provide your organization with expert on-demand cybersecurity expertise and advice.
We will help you tackle your key cybersecurity initiatives and set you up for long-term meaningful success.
Here's how it typically works:

Align on goals and assess essential assets, systems and data.

Coordinate comprehensive remediation plans for swift risk reduction and support urgent tasks.

Collaborate on a comprehensive cybersecurity plan to continuously level up.
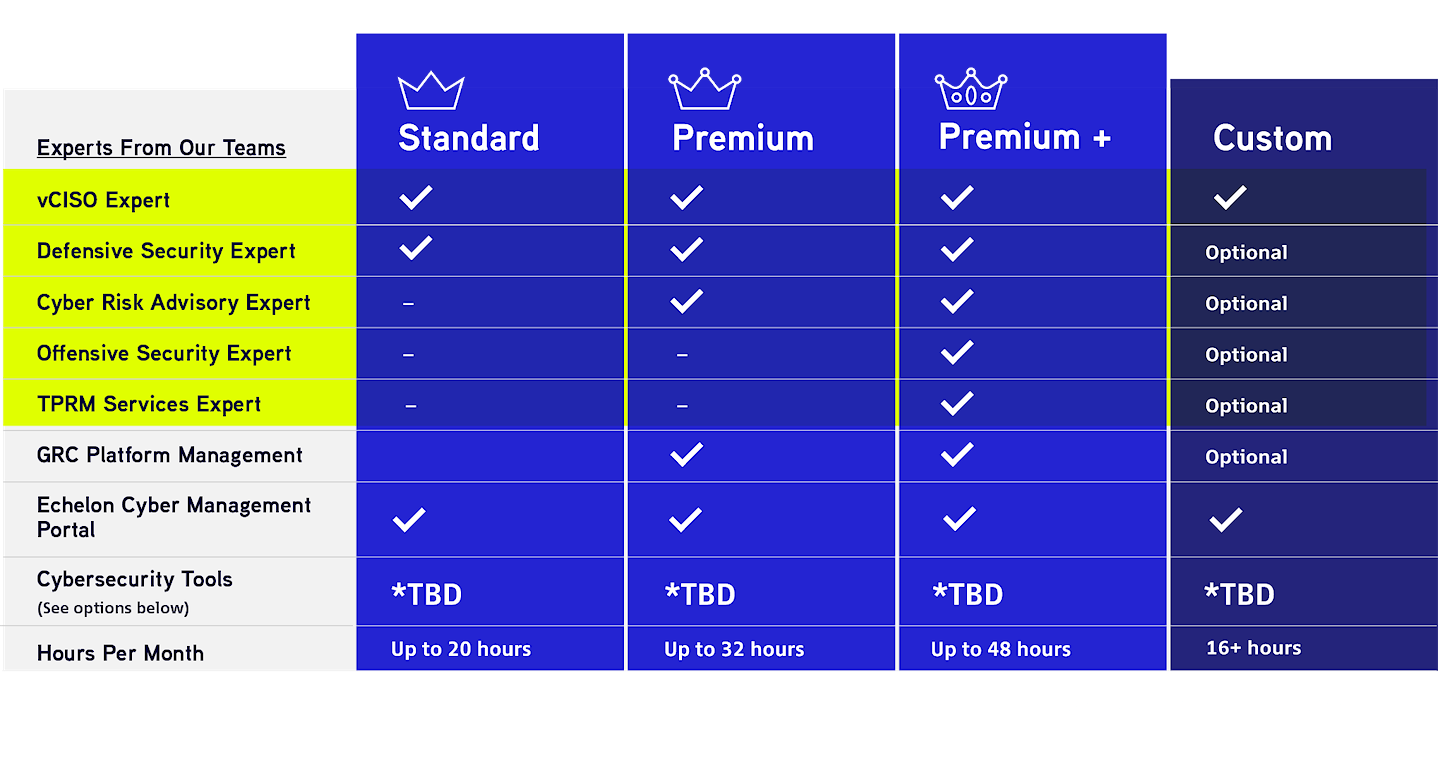
Our pricing combines vCISO advisory with resources and security services from our other cybersecurity teams, designed to meet your specific needs. Our three most popular packages include Standard, Premium and Premium Plus, but we will always customize a package for your organization.
In addition to the cybersecurity services and custom cyber portal, we can evaluate your current security platforms and identify the right tools for your unique needs.
We foster deep and strategic relationships with the industry's top vendors. These partnerships enable us to provide you with cutting-edge technologies combined with our expert insights to fuel your growth.
Examples include:
We are a companion in your cybersecurity journey,
delivering valuable outcomes and deliverables tailored to
fortify your cybersecurity defenses and compliance posture.
Cybersecurity Roadmap
Framework Management and Tracking
Policy Development and Management
Security Discoveries, Reviews, and System Hardening
Gap Identification
Current State Analysis
Compliance Support and Management
Vendor Risk Assessments and Due Diligence Responses
Regular Business Meeting and Audit Support
Cybersecurity and Compliance Reporting
Vulnerability Management
Security Tool Review and Tuning
Incident Response Planning and Tabletop Exercises
Keep Abreast of Evolving Threats and Compliance Requirements
Present to Key Stakeholders
Security Planning and Budgeting
Security Tool Selection
Penetration Tests, Assessments, and Remediation Support
Risk Management
System/Application/Data Security Practices and Processes
Security Awareness Training
At Echelon, we are not just a cybersecurity service provider - we are your trusted partner in creating a secure digital pathway for your business.
We're dedicated to delivering an exceptionally high level of service for your unique cybersecurity needs. Our team is a vibrant blend of dedicated, passionate, and top-notch cybersecurity talent, all geared towards one goal - your cybersecurity resilience.
We are your partner, committed to propelling your business securely into the digital future.
Client-Centric Excellence: Your satisfaction isn’t just a goal; it’s our benchmark of success. We thrive on open communication and transparency, ensuring you are always in the loop with the state of your cybersecurity landscape.
Quality at its Core: Every touchpoint with us is designed to exceed expectations, ensuring you get the maximum value out of our services.
Tailored Cybersecurity Program: We don’t believe in one-size-fits-all. Our services are meticulously tailored to offer an effective and efficient cybersecurity solution aligned with your business objectives.
Flexible Service Plans: Our service plans are as flexible as your needs, ensuring a perfect fit for your budget and cybersecurity goals.
Continual Growth and Improvement: As a firm, we are on a continual trajectory of growth and improvement, always evolving to ensure our services are in sync with the latest cybersecurity threats and compliance requirements.